Bitcoin is a new currency that was created in 2009 by an unknown person using the alias Satoshi Nakamoto. Transactions are made with no middle men – meaning, no banks! There are no transaction fees and no need to give your real name. More merchants are beginning to accept them: You can buy webhosting services, pizza or even manicures.

Why Bitcoins?
Bitcoins can be used to buy merchandise anonymously. In addition, international payments are easy and cheap because bitcoins are not tied to any country or subject to regulation. Small businesses may like them because there are no credit card fees. Some people just buy bitcoins as an investment, hoping that they’ll go up in value.
Acquiring Bitcoins
Buy on an Exchange
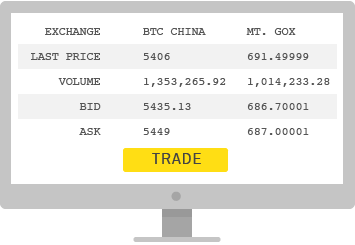
Several marketplaces called “bitcoin exchanges” allow people to buy or sell bitcoins using different currencies. Mt. Gox is the largest bitcoin exchange.
Several marketplaces called “bitcoin exchanges” allow people to buy or sell bitcoins using different currencies. Mt. Gox is the largest bitcoin exchange.
Transfers
People can send bitcoins to each other using mobile apps or their computers. It’s similar to sending cash digitally.
People can send bitcoins to each other using mobile apps or their computers. It’s similar to sending cash digitally.
Mining
People compete to “mine” bitcoins using computers to solve complex math puzzles. This is how bitcoins are created. Currently, a winner is rewarded with 25 bitcoins roughly every 10 minutes.
People compete to “mine” bitcoins using computers to solve complex math puzzles. This is how bitcoins are created. Currently, a winner is rewarded with 25 bitcoins roughly every 10 minutes.
Owning Bitcoins
Bitcoins are stored in a “digital wallet,” which exists either in the cloud or on a user’s computer. The wallet is a kind of virtual bank account that allows users to send or receive bitcoins, pay for goods or save their money. Unlike bank accounts, bitcoin wallets are not insured by the FDIC.
Wallet in cloud: Servers have been hacked. Companies have fled with clients’ Bitcoins.
Wallet on computer: You can accidentally delete them. Viruses could destroy them.
Anonymity

Though each bitcoin transaction is recorded in a public log, names of buyers and sellers are never revealed – only their wallet IDs. While that keeps bitcoin users’ transactions private, it also lets them buy or sell anything without easily tracing it back to them. That’s why it has become the currency of choice for people online buying drugs or other illicit activities.
Future in question
No one knows what will become of bitcoin. It is mostly unregulated, but that could change. Governments are concerned about taxation and their lack of control over the currency.
How to use Bitcoin?
1. Inform yourself
Some things you need to know
If you are about to explore Bitcoin, there are a few things you should know. Bitcoin lets you exchange money in a different way than with usual banks. As such, you should take time to inform yourself before using Bitcoin for any serious transaction. Bitcoin should be treated with the same care as your regular wallet, or even more in some cases!
 Securing your wallet
Securing your wallet
Like in real life, your wallet must be secured. Bitcoin makes it possible to transfer value anywhere in a very easy way and it allows you to be in control of your money. Such great features also come with great security concerns. At the same time, Bitcoin can provide very high levels of security if used correctly. Always remember that it is your responsibility to adopt good practices in order to protect your money. Read more about securing your wallet.
 Bitcoin price is volatile
Bitcoin price is volatile
The price of a bitcoin can unpredictably increase or decrease over a short period of time due to its young economy, novel nature, and sometimes illiquid markets. Consequently, keeping your savings with Bitcoin is not recommended at this point. Bitcoin should be seen like a high risk asset, and you should never store money that you cannot afford to lose with Bitcoin. If you receive payments with Bitcoin, many service providers can convert them to your local currency.
 Bitcoin payments are irreversible
Bitcoin payments are irreversible
Any transaction issued with Bitcoin cannot be reversed, they can only be refunded by the person receiving the funds. That means you should take care to do business with people and organizations you know and trust, or who have an established reputation. For their part, businesses need to keep control of the payment requests they are displaying to their customers. Bitcoin can detect typos and usually won't let you send money to an invalid address by mistake. Additional services might exist in the future to provide more choice and protection for the consumer.
 Bitcoin is not anonymous
Bitcoin is not anonymous
Some effort is required to protect your privacy with Bitcoin. All Bitcoin transactions are stored publicly and permanently on the network, which means anyone can see the balance and transactions of any Bitcoin address. However, the identity of the user behind an address remains unknown until information is revealed during a purchase or in other circumstances. This is one reason why Bitcoin addresses should only be used once. Always remember that it is your responsibility to adopt good practices in order to protect your privacy. Read more about protecting your privacy.
 Unconfirmed transactions aren't secure
Unconfirmed transactions aren't secure
Transactions don't start out as irreversible. Instead, they get a confirmation score that indicates how hard it is to reverse them (see table). Each confirmation takes between a few seconds and 90 minutes, with 10 minutes being the average. If the transaction pays too low a fee or is otherwise atypical, getting the first confirmation can take much longer.
| Confirmations | Lightweight wallets | Bitcoin Core |
|---|---|---|
| 0 | Only safe if you trust the person paying you | |
| 1 | Somewhat reliable | Mostly reliable |
| 3 | Mostly reliable | Highly reliable |
| 6 | Minimum recommendation for high-value bitcoin transfers | |
| 30 | Recommendation during emergencies to allow human intervention | |
 Bitcoin is still experimental
Bitcoin is still experimental
Bitcoin is an experimental new currency that is in active development. Each improvement makes Bitcoin more appealing but also reveals new challenges as Bitcoin adoption grows. During these growing pains you might encounter increased fees, slower confirmations, or even more severe issues. Be prepared for problems and consult a technical expert before making any major investments, but keep in mind that nobody can predict Bitcoin's future.
 Government taxes and regulations
Government taxes and regulations
Bitcoin is not an official currency. That said, most jurisdictions still require you to pay income, sales, payroll, and capital gains taxes on anything that has value, including bitcoins. It is your responsibility to ensure that you adhere to tax and other legal or regulatory mandates issued by your government and/or local municipalities.
2. Choose your wallet
Choose your Bitcoin wallet
Find your wallet and start making payments with merchants and users.
 Take time to educate yourself
Take time to educate yourself
Bitcoin is different from what you know and use every day. Before you start using Bitcoin for any serious transaction, be sure to read what you need to know and take appropriate steps to secure your wallet. Always remember that it is your responsibility to choose your wallet carefully and adopt good practices in order to protect your money.
3. Get Bitcoin
How to buy Bitcoin
There are several ways you can buy Bitcoin.
Use a Bitcoin Exchange
Our Bitcoin Exchange page, lists many different businesses that can help you buy Bitcoin using your bank account.
Discover people selling Bitcoin in your community
Local Bitcoins lets you search and browse through various sellers of Bitcoin in your area. Sellers have reviews and feedback scores to help you choose.
Use a Bitcoin ATM
Bitcoin ATMs work like a regular ATM, except they allow you to deposit and withdrawal money so that you can buy and sell Bitcoin. Coin ATM Radar has an interactive map to help you find the closest Bitcoin ATM near you.
4. Spend Bitcoin
Spending Bitcoin
There are thousands of businesses, across the globe, that accept Bitcoin.
Find products for sale online
One common use for Bitcoin is making purchases online. There are hundreds of online shops and retailers that accept Bitcoin. Using a search engine like Spendabit you can search through millions of products, all available for purchase with bitcoins.
Navigate a business directory
You can also find many businesses listed in online directories.
Find local businesses
There are also many local businesses, like cafes and restaurants, that accept Bitcoin. You can use Coinmap.org to browse thousands of businesses across the globe.
What is Blockchain Technology?
Is blockchain technology the new internet?
The blockchain is an undeniably ingenious invention – the brainchild of a person or group of people known by the pseudonym, Satoshi Nakamoto. But since then, it has evolved into something greater, and the main question every single person is asking is: What is Blockchain?
By allowing digital information to be distributed but not copied, blockchain technology created the backbone of a new type of internet. Originally devised for the digital currency, Bitcoin, the tech community is now finding other potential uses for the technology.
Bitcoin has been called “digital gold,” and for a good reason. To date, the total value of the currency is close to $9 billion US. And blockchains can make other types of digital value. Like the internet (or your car), you don’t need to know how the blockchain works to use it. However, having a basic knowledge of this new technology shows why it’s considered revolutionary. So, we hope you enjoy this, what is Blockchain guide.
What is Blockchain Technology?

“The blockchain is an incorruptible digital ledger of economic transactions that can be programmed to record not just financial transactions but virtually everything of value.”
Don & Alex Tapscott, authors Blockchain Revolution (2016)
Don & Alex Tapscott, authors Blockchain Revolution (2016)
A distributed database
Picture a spreadsheet that is duplicated thousands of times across a network of computers. Then imagine that this network is designed to regularly update this spreadsheet and you have a basic understanding of the blockchain.
Information held on a blockchain exists as a shared — and continually reconciled — database. This is a way of using the network that has obvious benefits. The blockchain database isn’t stored in any single location, meaning the records it keeps are truly public and easily verifiable. No centralized version of this information exists for a hacker to corrupt. Hosted by millions of computers simultaneously, its data is accessible to anyone on the internet.
To go in deeper with the Google spreadsheet analogy, I would like you to read this piece from a blockchain specialist.
Blockchain as Google Docs

“The traditional way of sharing documents with collaboration is to send a Microsoft Word document to another recipient, and ask them to make revisions to it. The problem with that scenario is that you need to wait until receiving a return copy before you can see or make other changes because you are locked out of editing it until the other person is done with it. That’s how databases work today. Two owners can’t be messing with the same record at once.That’s how banks maintain money balances and transfers; they briefly lock access (or decrease the balance) while they make a transfer, then update the other side, then re-open access (or update again).With Google Docs (or Google Sheets), both parties have access to the same document at the same time, and the single version of that document is always visible to both of them. It is like a shared ledger, but it is a shared document. The distributed part comes into play when sharing involves a number of people.
Imagine the number of legal documents that should be used that way. Instead of passing them to each other, losing track of versions, and not being in sync with the other version, why can’t *all* business documents become shared instead of transferred back and forth? So many types of legal contracts would be ideal for that kind of workflow.You don’t need a blockchain to share documents, but the shared documents analogy is a powerful one.”
William Mougayar, Venture advisor, 4x entrepreneur, marketer, strategist and blockchain specialist
Blockchain Durability and robustness
Blockchain technology is like the internet in that it has a built-in robustness. By storing blocks of information that are identical across its network, the blockchain cannot:
- Be controlled by any single entity.
- Has no single point of failure.
Bitcoin was invented in 2008. Since that time, the Bitcoin blockchain has operated without significant disruption. (To date, any of problems associated with Bitcoin have been due to hacking or mismanagement. In other words, these problems come from bad intention and human error, not flaws in the underlying concepts.)
The internet itself has proven to be durable for almost 30 years. It’s a track record that bodes well for blockchain technology as it continues to be developed.

“As revolutionary as it sounds, Blockchain truly is a mechanism to bring everyone to the highest degree of accountability. No more missed transactions, human or machine errors, or even an exchange that was not done with the consent of the parties involved. Above anything else, the most critical area where Blockchain helps is to guarantee the validity of a transaction by recording it not only on a main register but a connected distributed system of registers, all of which are connected through a secure validation mechanism.”
– Ian Khan, TEDx Speaker | Author | Technology Futurist
Transparent and incorruptible
The blockchain network lives in a state of consensus, one that automatically checks in with itself every ten minutes. A kind of self-auditing ecosystem of a digital value, the network reconciles every transaction that happens in ten-minute intervals. Each group of these transactions is referred to as a “block”. Two important properties result from this:
- Transparency data is embedded within the network as a whole, by definition it is public.
- It cannot be corrupted altering any unit of information on the blockchain would mean using a huge amount of computing power to override the entire network.
In theory, this could be possible. In practice, it’s unlikely to happen. Taking control of the system to capture Bitcoins, for instance, would also have the effect of destroying their value.

“Blockchain solves the problem of manipulation. When I speak about it in the West, people say they trust Google, Facebook, or their banks. But the rest of the world doesn’t trust organizations and corporations that much — I mean Africa, India, the Eastern Europe, or Russia. It’s not about the places where people are really rich. Blockchain’s opportunities are the highest in the countries that haven’t reached that level yet.”
Vitalik Buterin, inventor of Ethereum
Vitalik Buterin, inventor of Ethereum
A network of nodes
A network of so-called computing “nodes” make up the blockchain.
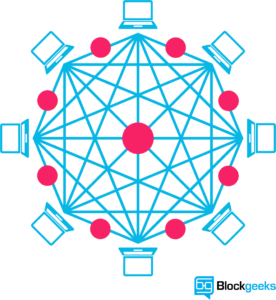
Node
(computer connected to the blockchain network using a client that performs the task of validating and relaying transactions) gets a copy of the blockchain, which gets downloaded automatically upon joining the blockchain network.
Together they create a powerful second-level network, a wholly different vision for how the internet can function.
Every node is an “administrator” of the blockchain, and joins the network voluntarily (in this sense, the network is decentralized). However, each one has an incentive for participating in the network: the chance of winning Bitcoins.
Nodes are said to be “mining” Bitcoin, but the term is something of a misnomer. In fact, each one is competing to win Bitcoins by solving computational puzzles. Bitcoin was the raison d’etre of the blockchain as it was originally conceived. It’s now recognized to be only the first of many potential applications of the technology.
There are an estimated 700 Bitcoin-like cryptocurrencies (exchangeable value tokens) already available. As well, a range of other potential adaptations of the original blockchain concept are currently active, or in development.

“Bitcoin has the same character a fax machine had. A single fax machine is a doorstop. The world where everyone has a fax machine is an immensely valuable thing.”
Larry Summers, Former US Secretary of the Treasury
Larry Summers, Former US Secretary of the Treasury
The idea of decentralization
By design, the blockchain is a decentralized technology.
Anything that happens on it is a function of the network as a whole. Some important implications stem from this. By creating a new way to verify transactions aspects of traditional commerce could become unnecessary. Stock market trades become almost simultaneous on the blockchain, for instance — or it could make types of record keeping, like a land registry, fully public. And decentralization is already a reality.
A global network of computers uses blockchain technology to jointly manage the database that records Bitcoin transactions. That is, Bitcoin is managed by its network, and not any one central authority. Decentralization means the network operates on a user-to-user (or peer-to-peer) basis. The forms of mass collaboration this makes possible are just beginning to be investigated.

“I think decentralized networks will be the next huge wave in technology.”
Melanie Swan, author Blockchain: Blueprint for a New Economy (2015)
Melanie Swan, author Blockchain: Blueprint for a New Economy (2015)
Who will use the blockchain?
As web infrastructure, you don’t need to know about the blockchain for it to be useful in your life.
Currently, finance offers the strongest use cases for the technology. International remittances, for instance. The World Bank estimates that over $430 billion US in money transfers were sent in 2015. And at the moment there is a high demand for blockchain developers.
The blockchain potentially cuts out the middleman for these types of transactions. Personal computing became accessible to the general public with the invention of the Graphical User Interface (GUI), which took the form of a “desktop”. Similarly, the most common GUI devised for the blockchain are the so-called “wallet” applications, which people use to buy things with Bitcoin, and store it along with other cryptocurrencies.
Transactions online are closely connected to the processes of identity verification. It is easy to imagine that wallet apps will transform in the coming years to include other types of identity management.

“Online identity and reputation will be decentralized. We will own the data that belongs to us.”
William Mougayar, author The Business Blockchain: Promise, Practice, and Application of the Next Internet Technology (2016)
William Mougayar, author The Business Blockchain: Promise, Practice, and Application of the Next Internet Technology (2016)
The Blockchain & Enhanced security
By storing data across its network, the blockchain eliminates the risks that come with data being held centrally.
Its network lacks centralized points of vulnerability that computer hackers can exploit. Today’s internet has security problems that are familiar to everyone. We all rely on the “username/password” system to protect our identity and assets online. Blockchain security methods use encryption technology.
The basis for this are the so-called public and private “keys”. A “public key” (a long, randomly-generated string of numbers) is a users’ address on the blockchain. Bitcoins sent across the network gets recorded as belonging to that address. The “private key” is like a password that gives its owner access to their Bitcoin or other digital assets. Store your data on the blockchain and it is incorruptible. This is true, although protecting your digital assets will also require safeguarding of your private key by printing it out, creating what’s referred to as a paper wallet.
A second-level network
With blockchain technology, the web gains a new layer of functionality.
Already, users can transact directly with one another — Bitcoin transactions in 2016 averaged over $200,000 US per day. With the added security brought by the blockchain new internet business are on track to unbundle the traditional institutions of finance.
Goldman Sachs believes that blockchain technology holds great potential especially to optimize clearing and settlements, and could represent global savings of up to $6bn per year.

“2017 will be a pivotal year for blockchain tech. Many of the startups in the space will either begin generating revenue – via providing products the market demands/values – or vaporize due to running out of cash. In other words, 2017 should be the year where there is more implementation of products utilizing blockchain tech, and less talk about blockchain tech being the magical pixie dust that can just be sprinkled atop everything. Of course, from a customers viewpoint, this will not be obvious as blockchain tech should dominantly be invisible – even as its features and functionality improve peoples’/business’ lives. I personally am familiar with a number of large-scale blockchain tech use cases that are launching soon/2017. This implementation stage, which 2017 should represent, is a crucial step in the larger adoption of blockchain tech, as it will allow skeptics to see the functionality, rather than just hear of its promise.”
– George Howard, Associate Professor Brown University, Berklee College of Music and Founder of George Howard Strategic
The Blockchain a New Web 3.0?
The blockchain gives internet users the ability to create value and authenticates digital information. What will new business applications result?
Smart contracts
Distributed ledgers enable the coding of simple contracts that will execute when specified conditions are met. Ethereum is an open source blockchain project that was built specifically to realize this possibility. Still, in its early stages, Ethereum has the potential to leverage the usefulness of blockchains on a truly world-changing scale.At the technology’s current level of development, smart contracts can be programmed to perform simple functions. For instance, a derivative could be paid out when a financial instrument meets certain benchmark, with the use of blockchain technology and Bitcoin enabling the payout to be automated.The sharing economy
With companies like Uber and AirBnB flourishing, the sharing economy is already a proven success. Currently, however, users who want to hail a ride-sharing service have to rely on an intermediary like Uber. By enabling peer-to-peer payments, the blockchain opens the door to direct interaction between parties — a truly decentralized sharing economy results.An early example, OpenBazaar uses the blockchain to create a peer-to-peer eBay. Download the app onto your computing device, and you can transact with OpenBazzar vendors without paying transaction fees. The “no rules” ethos of the protocol means that personal reputation will be even more important to business interactions than it currently is on eBay.Crowdfunding
Crowdfunding initiatives like Kickstarter and Gofundme are doing the advance work for the emerging peer-to-peer economy. The popularity of these sites suggests people want to have a direct say in product development. Blockchains take this interest to the next level, potentially creating crowd-sourced venture capital funds.In 2016, one such experiment, the Ethereum-based DAO (Decentralized Autonomous Organization), raised an astonishing $200 million USD in just over two months. Participants purchased “DAO tokens” allowing them to vote on smart contract venture capital investments (voting power was proportionate to the number of DAO they were holding). A subsequent hack of project funds proved that the project was launched without proper due diligence, with disastrous consequences. Regardless, the DAO experiment suggests the blockchain has the potential to usher in “a new paradigm of economic cooperation.”Governance
By making the results fully transparent and publicly accessible, distributed database technology could bring full transparency to elections or any other kind of poll taking. Ethereum-based smart contracts help to automate the process.The app, Boardroom, enables organizational decision-making to happen on the blockchain. In practice, this means company governance becomes fully transparent and verifiable when managing digital assets, equity or information.Supply chain auditing
Consumers increasingly want to know that the ethical claims companies make about their products are real. Distributed ledgers provide an easy way to certify that the backstories of the things we buy are genuine. Transparency comes with blockchain-based timestamping of a date and location — on ethical diamonds, for instance — that corresponds to a product number.The UK-based Provenance offers supply chain auditing for a range of consumer goods. Making use of the Ethereum blockchain, a Provenance pilot project ensures that fish sold in Sushi restaurants in Japan has been sustainably harvested by its suppliers in Indonesia.File storage
Decentralizing file storage on the internet brings clear benefits. Distributing data throughout the network protects files from getting hacked or lost.Inter Planetary File System (IPFS) makes it easy to conceptualize how a distributed web might operate. Similar to the way a bittorrent moves data around the internet, IPFS gets rid of the need for centralized client-server relationships (i.e., the current web). An internet made up of completely decentralized websites has the potential to speed up file transfer and streaming times. Such an improvement is not only convenient. It’s a necessary upgrade to the web’s currently overloaded content-delivery systems.Prediction markets
The crowdsourcing of predictions on event probability is proven to have a high degree of accuracy. Averaging opinions cancels out the unexamined biases that distort judgment. Prediction markets that payout according to event outcomes are already active. Blockchains are a “wisdom of the crowd” technology that will no doubt find other applications in the years to come.Still, in Beta, the prediction market application Augur makes share offerings on the outcome of real-world events. Participants can earn money by buying into the correct prediction. The more shares purchased in the correct outcome, the higher the payout will be. With a small commitment of funds (less than a dollar), anyone can ask a question, create a market based on a predicted outcome, and collect half of all transaction fees the market generates.Protection of intellectual property
As is well known, digital information can be infinitely reproduced — and distributed widely thanks to the internet. This has given web users globally a goldmine of free content. However, copyright holders have not been so lucky, losing control over their intellectual property and suffering financially as a consequence. Smart contracts can protect copyright and automate the sale of creative works online, eliminating the risk of file copying and redistribution.Mycelia uses the blockchain to create a peer-to-peer music distribution system. Founded by the UK singer-songwriter Imogen Heap, Mycelia enables musicians to sell songs directly to audiences, as well as license samples to producers and divvy up royalties to songwriters and musicians — all of these functions being automated by smart contracts. The capacity of blockchains to issue payments in fractional cryptocurrency amounts (micropayments) suggests this use case for the blockchain has a strong chance of success.Internet of Things (IoT)
What is the IoT? The network-controlled management of certain types of electronic devices — for instance, the monitoring of air temperature in a storage facility. Smart contracts make the automation of remote systems management possible. A combination of software, sensors, and the network facilitates an exchange of data between objects and mechanisms. The result increases system efficiency and improves cost monitoring.The biggest players in manufacturing, tech and telecommunications are all vying for IoT dominance. Think Samsung, IBM and AT&T. A natural extension of existing infrastructure controlled by incumbents, IoT applications will run the gamut from predictive maintenance of mechanical parts to data analytics, and mass-scale automated systems management.Neighbourhood Microgrids
Blockchain technology enables the buying and selling of the renewable energy generated by neighborhood microgrids. When solar panels make excess energy, Ethereum-based smart contracts automatically redistribute it. Similar types of smart contract automation will have many other applications as the IoT becomes a reality.Located in Brooklyn, Consensys is one of the foremost companies globally that is developing a range of applications for Ethereum. One project they are partnering on is Transactive Grid, working with the distributed energy outfit, LO3. A prototype project currently up and running uses Ethereum smart contracts to automate the monitoring and redistribution of microgrid energy. This so-called “intelligent grid” is an early example of IoT functionality.Identity management
There is a definite need for better identity management on the web. The ability to verify your identity is the lynchpin of financial transactions that happen online. However, remedies for the security risks that come with web commerce are imperfect at best. Distributed ledgers offer enhanced methods for proving who you are, along with the possibility to digitize personal documents. Having a secure identity will also be important for online interactions — for instance, in the sharing economy. A good reputation, after all, is the most important condition for conducting transactions online.Developing digital identity standards is proving to be a highly complex process. Technical challenges aside, a universal online identity solution requires cooperation between private entities and government. Add to that the need to navigate legal systems in different countries and the problem becomes exponentially difficult. E-Commerce on the internet currently relies on the SSL certificate (the little green lock) for secure transactions on the web. Netki is a startup that aspires to create an SSL standard for the blockchain. Having recently announced a $3.5 million seed round, Netki expects a product launch in early 2017.AML and KYC
Anti-money laundering (AML) and know your customer (KYC) practices have a strong potential for being adapted to the blockchain. Currently, financial institutions must perform a labour intensive multi-step process for each new customer. KYC costs could be reduced through cross-institution client verification, and at the same time increase monitoring and analysis effectiveness.Startup Polycoin has an AML/KYC solution that involves analysing transactions. Those transactions identified as being suspicious are forwarded on to compliance officers. Another startup Tradle is developing an application called Trust in Motion (TiM). Characterized as an “Instagram for KYC”, TiM allows customers to take a snapshot of key documents (passport, utility bill, etc.). Once verified by the bank, this data is cryptographically stored on the blockchain.Data management
Today, in exchange for their personal data people can use social media platforms like Facebook for free. In future, users will have the ability to manage and sell the data their online activity generates. Because it can be easily distributed in small fractional amounts, Bitcoin — or something like it — will most likely be the currency that gets used for this type of transaction.The MIT project Enigma understands that user privacy is the key precondition for creating of a personal data marketplace. Enigma uses cryptographic techniques to allow individual data sets to be split between nodes, and at the same time run bulk computations over the data group as a whole. Fragmenting the data also makes Enigma scalable (unlike those blockchain solutions where data gets replicated on every node). A Beta launch is promised within the next six months.Land title registration
As Publicly-accessible ledgers, blockchains can make all kinds of record-keeping more efficient. Property titles are a case in point. They tend to be susceptible to fraud, as well as costly and labour intensive to administer.A number of countries are undertaking blockchain-based land registry projects. Honduras was the first government to announce such an initiative in 2015, although the current status of that project is unclear. This year, the Republic of Georgia cemented a deal with the Bitfury Group to develop a blockchain system for property titles. Reportedly, Hernando de Soto, the high-profile economist and property rights advocate, will be advising on the project. Most recently, Sweden announced it was experimenting with a blockchain application for property titles.Stock trading
The potential for added efficiency in share settlement makes a strong use case for blockchains in stock trading. When executed peer-to-peer, trade confirmations become almost instantaneous (as opposed to taking three days for clearance). Potentially, this means intermediaries — such as the clearing house, auditors and custodians — get removed from the process.Numerous stock and commodities exchanges are prototyping blockchain applications for the services they offer, including the ASX (Australian Securities Exchange), the Deutsche Börse (Frankfurt’s stock exchange) and the JPX (Japan Exchange Group). Most high profile because the acknowledged first mover in the area, is the Nasdaq’s Linq, a platform for private market trading (typically between pre-IPO startups and investors). A partnership with the blockchain tech company Chain, Linq announced the completion of it its first share trade in 2015. More recently, Nasdaq announced the development of a trial blockchain project for proxy voting on the Estonian Stock Market.
Blockchain Scalability: When, Where, How?
Blockchain Scalability, a very real problem!
Cryptocurrencies are becoming more and more mainstream. In fact, let’s check out how popular bitcoin and ethereum have gotten over time. This is a graph of the number of daily bitcoin transactions tracked over the years:
Image Courtesy: Wikipedia
And here we have the number of Ethereum transactions per month over the years:
Image Courtesy: Etherscan
Now, this may look very impressive, but here is the thing, the initial design of cryptocurrencies was not meant for widespread use and adaptation. While it was manageable when the number of transactions was less, as they have gotten more popular a host of issues have come up.
The scalability problem of cryptocurrencies
For bitcoin and ethereum to compete with more mainstream systems like visa and paypal, they need to seriously step up their game when it comes to transaction times. While paypal manages 193 transactions per second and visa manages 1667 transactions per second, Ethereum does only 20 transactions per second while bitcoin manages a whopping 7 transactions per second! The only way that these numbers can be improved is if they work on their scalability.
If we were to categorize the main scalability problems in the cryptocurrencies, they would be:
- The time is taken to put a transaction in the block.
- The time is taken to reach a consensus.
The Time Taken To Put A Transaction In The Block
In bitcoin and ethereum, a transaction goes through when a miner puts the transaction data in the blocks that they have mined. So suppose Alice wants to send 4 BTC to Bob, she will send this transaction data to the miners, the miner will then put it in their block and the transaction will be deemed complete.
However, as bitcoin becomes more and more popular, this becomes more time-consuming. Plus, there is also the small matter of transactions fees. You see, when miners mine a block, they become temporary dictators of that block. If you want your transactions to go through, you will have to pay a toll to the miner in charge. This “toll” is called transaction fees.
The higher the transaction fees, the faster the miners will put them up in their block. While this is ok for people who have a huge repository of bitcoins, it might not be the most financially viable options. In fact, here is an interesting study for you. This is the amount of time that people had to wait if they paid the lowest possible transaction fee:
If you pay the lowest possible transaction fees, then you will have to wait for a median time of 13 mins for your transaction to go through.
More often than not, the transactions had to wait until a new block was mined (which is 10 mins in bitcoin), because the older blocks would fill up with transactions. Bitcoin has a size limit of 1 mb (this will be expanded on later) which severely limits its transaction carrying capacity.
Ok, so what about Ethereum?
Theoretically speaking, Ethereum is supposed to process 1000 transactions per second. However, in practice, Ethereum is limited by 6.7 million gas limit on each block.
To understand what “gas” means, think of this situation. Alice has issued a smart contract for Bob. Bob sees that the elements in the contract will cost X amount of gas. Gas meaning the amount of computational effort on Bob’s part. Accordingly, he will charge Alice for the amount of Gas he used up.
This is what the gas price chart looks like:
Image courtesy: Etherscan.
What does this mean for Blockchain scalability?
Since each block has a gas limit, the miners can only add transactions whose gas requirements add up to something which is equal to or less than the gas limit of the block.
Image courtesy: Hackernoon
Once again, a number of transactions going through is limited.
The Time Taken To Reach A Consensus
Currently, all blockchain based currencies are structured as a peer-to-peer network. The participants, aka the nodes, are not given any extra special privileges. The idea is to create an egalitarian network. There is no central authority and nor is there any hierarchy. It is a flat topology.
All decentralized cryptocurrencies are structured like this because of a simple reason, to stay true to their philosophy. The idea is to have a currency system, where everyone is treated as an equal and there is no governing body, which can determine the value of the currency based on a whim. This is true for both bitcoin and Ethereum.
Now, if there is no central entity, how would everyone in the system get to know that a certain transaction has happened? The network follows the gossip protocol. Think of how gossip spreads. Suppose Alice sent 3 ETH to Bob. The nodes nearest to her will get to know of this, and then they will tell the nodes closest to them, and then they will tell their neighbors, and this will keep on spreading out until everyone knows. Nodes are basically your nosy, annoying relatives.
Remember, the nodes follow a trustless system. What this means is, just because node A says that a transaction is valid doesn’t mean that node B will believe it to be so. Node B will do their own set of calculations to see whether the transaction is actually valid or not. This means, that every node must have their own copy of the blockchain to help them do so. As you can imagine, this makes the whole process very slow.
The problem is, that unlike other pieces of technology, the more the number of nodes increases in a cryptocurrency network, the slower the whole process becomes. Consensus happens in a linear manner, meaning, suppose there are 3 nodes A, B and C.
For consensus to occur, first A would do the calculations and verify and then B will do the same and then C.
However, if there is a new node in the system called “D”, that would add one more node to the consensus system, which will increase the overall time period. As cryptocurrencies has become more popular, the transaction times have gotten slower.
This is especially a problem with Ethereum, because it has the most number of nodes among all cryptocurrencies. Thanks to the ICO craze, everyone wants to have a piece of Ethereum, which has significantly increased the number of nodes in its network. In fact, as of May 2017, Ethereum had 25,000 nodes as compared to Bitcoin’s 7000!! That’s more than 3 times. In fact, the number of nodes from April to May increase by 81%…that’s nearly double!
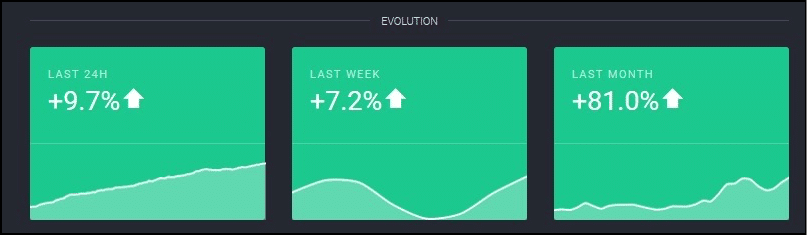
Image Courtesy: Trust Nodes.
So what are the solutions to the Blockchain scalability issues?
Both Ethereum and Bitcoins have come up with a host of solutions which have either already been or are going to be implemented. Let’s go through some of the major ones.
The ones that we will be covering are:
- Segwit.
- Block Size Increase.
- Sharding.
- Proof Of Stake.
- Off Chain State Channels.
- Plasma
Segwit (Exclusive only to bitcoin)
Blockstream’s Dr Peter Wiulle envisioned Segwit as one of the features of the sidechain which will run parallel to the main bitcoin blockchain.
Activating Segwit aka Segregated Witness would mean that all the signature data of each and every transaction will move from the main chain to the side chain. What do we mean by signature data? Let’s look at the behind the scenes data of a transaction:
The transaction details code
This is what the transaction looks like in the code form. Suppose Alice wants to send 0.0015 BTC to Bob and in order to do so, she sends inputs which are worth 0.0015770 BTC. This is what the transaction detail looks like:
Image courtesy: djp3 youtube channel.
The first thing that you see:
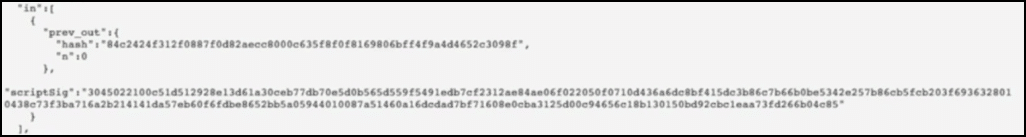
Is the name of the Transaction aka the hash of the input and output value.
- Vin_sz is the number of input data, since Alice is sending the data using only one of her previous transactions, it is 1.
- Vout_sz is 2 because the only outputs are Bob and the change.
This is the Input data:
See the input data? Alice is only using one input transaction as vin_sz is 1. The input data is 0.0015770 BTC.
Below the input data is her signature data (Remember this for the next section)
Underneath all this is the output data:
- The first part of the data signifies that Bob is getting 0.0015 BTC.
- The second part signifies that 0.00005120 BTC is what Alice is getting back as change.
- Now, remember that our input data was 0.0015770 BTC? This is greater than (0.0015 + 0.00005120). The deficit of these two values is the transaction fee that the miners are collecting.
This is the anatomy of a simple transaction.
So what will happen on activating Segwit?
The problem with this signature data is that it is very bulky. In fact, 65% of the data taken up by the transaction is because of the signature. And this data is useful only for the initial verification process, it is not needed later on at all.
So what will happen on activating Segwit?
The signature data will move on from the main chain to the extended block in the parallel chain:
What this will do is that it’ll free up a lot of space in the block itself for more transactions.
It was envisioned that the signature data would be arranged in the form of a Merkle tree in the side chain. The Merkle root of the transactions was placed in the block along with the coinbase transaction (the first transaction in each block which basically signifies the block reward). However, on doing this, the developers stumbled upon something unexpected. They discovered that on putting the merkle root in that particular place they somehow increased the overall block size limit WITHOUT increasing the block size limit!
As of August 24, 2017 segwit was activated on bitcoin. Let’s see what Segwit had to say about that:
Image courtesy: segwit.co
Pros and Cons of Segwit
Pros of segwit:
- Increases a number of transactions that a block can take.
- Decreases transaction fees.
- Reduces the size of each individual transaction.
- Transactions can now be confirmed faster because the waiting time will decrease.
- Helps in the scalability of bitcoin.
- Since the number of transactions in each block will increase, it may increase the total overall fees that a miner may collect.
- Removes transaction malleability and aids in the activation of lightning protocol (more on this later)
- Removes the quadratic hashing problem: Quadratic hashing is an issue that comes along with block size increase. The problem is that in certain transactions, signature hashing scales quadratically
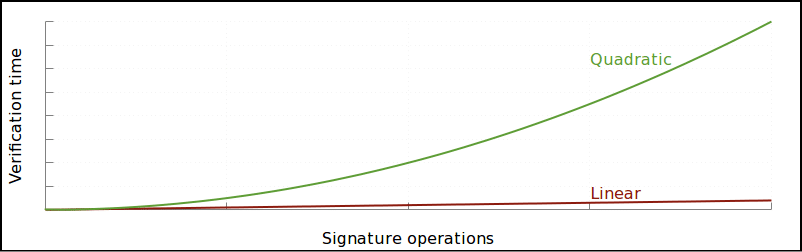
Image courtesy: Bitcoincore.org
Basically, doubling the amount of transactions in a block will double a number of transactions and that in turn will double the amount of signature data that will be inside each of those transactions. This would make the transactions even more bulky and increase the transaction time by a huge amount. This opens the gates for malicious parties who may want to spam the blockchain.
Segwit resolves this by changing the calculation of the signature hash and make the whole process more efficient as a result.
Cons of segwit:
- Miners will now get lesser transaction fees for each individual transaction.
- The implementation is complex and all the wallets will need to implement segwit themselves. There is a big chance that they may not get it right the first time.
- It will significantly increase the usage of resources since the capacity, transactions, bandwidth everything will increase.
- As the creation of Bitcoin Cash shows, it did ultimately split up the Bitcoin Core community.
- Another problem with Segwit is the maintenance. The sidechain containing the signature data will need to be maintained by miners as well. However, unlike the main blockchain, the miners have no financial benefits on doing so, it will need to be done pro-bono or some reward scheme needs to be thought of to incentivize the miners.
Block size Increase
Now, since the main problem of bitcoin and ethereum has been the limited blocksize, why don’t we just increase them? Bitcoin wasn’t supposed to have a 1 MB limit but then Satoshi was forced to put it because they didn’t want Bitcoin to be bogged down by spam transactions.
While this might sound like a good idea in practice, the implementation of this has been anything but. In fact, this has given birth to a lot of debate in the Bitcoin community with sides passionately arguing both for and against the block size increase. Let’s checkout some of these arguments:
Arguments against block size increase
- Miners will lose incentive because transaction fees will decrease: Since the block sizes will increase transactions will be easily inserted, which will significantly lower the transaction fees. There are fears that this may deincentivize the miners and they may move on to greener pastures. If the number of miners decrease then this will decrease the overall hashrate of bitcoin.
- Bitcoins shouldn’t be used for everyday purposes: Some members of the community don’t want bitcoin to be used for regular everyday transactions. These people feel that bitcoins have a higher purpose than just being regular everyday currency.
- It will split the community: A block size increase will inevitably cause a fork in the system which will make two parallel bitcoins and hence split the community in the process. This may destroy the harmony in the community.
- It will cause increased centralization: Since the network size will increase, the amount of processing power required to mine will increase as well. This will take out all the small mining pools and give mining powers exclusively to the large scale pools. This will in turn increase centralization which goes against the very essence of bitcoins.
Arguments for the block size increase
- Block size increase actually works to the miner’s benefit: Increased block size will mean increase transactions per block which will in turn increase the amount of transaction fees that a miner may make from mining a block.
- Bitcoin needs to grow more and be more accessible for the “common man”. If the block size doesn’t change then there is a very real possibility that the transactions fees will go higher and higher. When that happens, the common man will never be able to use it and it will be used exclusively only by the rich and big corporations. That has never been the purpose of bitcoin.
- The changes won’t happen all at once, they will gradually happen over time. The biggest fear that people have when it comes to the block size change is that too many things are going to be affected at the same time and that will cause major disruption. However, people who are “pro block size increase” think that that’s an unfounded fear as most of the changes will be dealt with over a period of time.
- There is a lot of support for block size increase already and people who don’t get with the times may get left behind.
- Segwit is not a permanent fix.
Anyway, on May 21 2017, the New York Agreement took place where it was decided that Segwit will be activated and the block sizes will increase to 2 mb.
Image courtesy: DCG article in Medium.
People who were not happy with the idea of Segwit activating forked away from the main chain and made Bitcoin Cash which has a block size limit of 8 mb.
A block size increase was also suggested for Ethereum but because of a lot of reasons people are not really keen on doing that in Ethereum as of writing:
- Firstly, the main thing that is hindering Ethereum’s scalability is the speed of consensus among nodes. Increasing the block size will still not solve this problem. In fact, as the number of transactions per block increases, the number of calculations and verifications per node will increase as well.
- In order to accommodate for more and more transactions, the block sizes need to be increased periodically. This will centralize the system more because normal computers and users won’t be able to download and preserve such bulky blockchains. This goes against the egalitarian spirit of a blockchain.
- Finally, block size increase will happen only via hardfork, which can split the community. The last time a major hardfork happened in Ethereum the entire community was divided and two separate currencies came about. People don’t really want this to happen again.
Proof Of Stake
The change from proof of work to proof of stake
One of biggest things happening right now is Ethereum’s shift from proof of work to proof of stake.
- Proof of work: This is the protocol that most cryptocurrencies like Ethereum and Bitcoin have been following so far. This means that miners “mine” cryptocurrencies by solving crypto-puzzles using dedicated hardware.
- Proof of stake: This protocol will make the entire mining process virtual. In this system we have validators instead of miners. The way it works is that as a validator, you will first have to lock up some of your ether as stake. After doing that you will then start validating blocks which basically means that if you see any blocks that you think can be appended to the blockchain, you can validate it by placing a bet on it. When and if, the block gets appended, you will get a reward proportional to the stake you have invested. If, however, you bet on the wrong or the malicious block, the stake that you have invested will be taken away from you.
To implement “proof of stake” Ethereum is going to use the Casper consensus algorithm. In the beginning it is going to be a hybrid style system where majority of the transactions will still be done the proof of work style while every 100th transaction is going to be proof of stake. What this will do is that it will provide a real world test for proof of stake on Ethereum’s platform. But what does that mean for Ethereum and what are the advantages of this protocol? Let’s take a look.
Advantages of proof of stake
- Lowers the overall energy and monetary cost: The world’s bitcoin miners spend around $50,000 per hour on electricity. That’s $1.2 million per day, $36 million per month and ~$450 million per year! Just put your head around those numbers and the amount of power being wasted. By using “Proof-of-stake” you are the making the whole process completely virtual and cutting off all these costs.
- No ASIC advantage: Since the whole process will be virtual, it wouldn’t depend on who has the better equipment or ASICs (application-specific integrated circuit).
- Makes 51% attack harder: 51% attack happens when a group of miners gain more than 50% of the world’s hashing power. Using proof of stake negates this attack.
- Malicious-free validators: Any validator who has their funds locked up in the blockchain would make sure that they are not adding any wrong or malicious blocks to the chain, because that would mean their entire stake invested would be taken away from them.
- Block creation: Makes the creation of newer blocks and the entire process faster. (More on this in the next section).
- Scalability: Makes the blockchain scalable by introducing the concept of “sharding” (More on this later.)
How does this help in Blockchain scalability.
Introducing proof-of-stake is going to make the blockchain a lot faster because it is much more simple to check who has the most stake then to see who has the most hashing power. This makes coming to a consensus much more simple. Plus, implementing a “proof of stake blockchain” is an integral part of Serenity, the 4th and final form of Ethereum (more on this in a bit.)
At the same time proof-of-stake makes the implementation of sharding easier. In a proof-of-work system it will be easier for an attacker to attack individual shards which may not have high hashrate.
Also, in POS miners won’t be getting a block fee, and they can only earn via transaction fees. This incentivizes them to increase the block size to get in more transactions (via gas management).
What is the future of proof of stake?
As of right now, Casper stage one is going to be implemented on the blockchain, wherein every 100th block will be checked via proof-of-stake. Yoichi Hirai from Ethereum foundations has been running casper scripts through mathematical bug detectors to make sure that it is completely bug free.
Eventually, the plan is to move majority of the block creation through proof-of-stake and the way they are planning to do that is….by entering the ice age. The “ice age” is a difficulty time bomb which is going to make mining exponentially more difficult. Having an impossibly high difficulty will greatly reduce the hash rate which in turn will reduce the speed of the entire blockchain and the DAPPS running on it. This will force everyone involved in Ethereum to move on to proof-of-stake.
However, this entire transition is not without its obstacles. One of the biggest fears that people have is that miners may forced a hardfork in the chain at a point before the ice age begins and then continue mining in that chain. This could be potentially disastrous because that would mean there could be 3 different chains of Ethereum running at the same time: Ethereum classic, Ethereum proof of work and Ethereum proof of stake.
This is currently all speculation. For now, the fact is that, for a scalable model, it is critical for Ethereum to use proof of stake to get the speed and the flexibility it requires.
Sharding
The biggest problem that Ethereum is facing is the speed of transaction verification. Each and every full node in the network has to download and save the entire blockchain. What sharding does is that it breaks down a transaction into shards and spreads it among the network. The nodes work on individual shards side-by-side. This in turn decreases the overall time taken.
Imagine that Ethereum has been split into thousands of islands. Each island can do its own thing. Each of the island has its own unique features and everyone belonging on that island i.e. the accounts, can interact with each other AND they can freely indulge in all its features. If they want to contact with other islands, they will have to use some sort of protocol.
So, the question is, how is that going to change the blockchain?
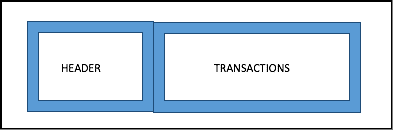
What does a normal block in bitcoin or Ethereum (pre-sharding) look like?
So, there is a block header and the body which contains all the transactions in the block. The Merkle root of all the transactions will be in the block header.
Now, think about this.
- Did bitcoin really need blocks?
- Did it really need a block chain??
- Satoshi could have simply made a chain of transactions by including the hash of the previous transaction in the newer transaction, making a “transaction chain” so to speak.
The reason why they arrange these transactions in a block is to create one level of interaction and make the whole process more scalable. What Ethereum suggests is that they change this into two levels of interaction.
The First Level
The first level is the transaction group. Each shard has its own group of transaction.
Image courtesy: Hackernoon
The transaction group is divided into the transaction group header and the transaction group body.
Transaction Group Header
- The header is divided into distinct left and right parts.
The Left Part:
- Shard ID: The ID of the shard that the transaction group belongs to.
- Pre state root: This the state of the root of shard 43 before the transactions were applied.
- Post state root: This is the state of the root of shard 43 after the transactions are applied.
- Receipt root: The receipt root after all the transactions in shard 43 are applied.
The Right Part:
- The right part is full of random validators who need to verify the transactions in the shard itself. They are all randomly chosen.
Transaction Group Body
- It has all the transaction IDs in the shard itself.
Properties of Level One
- Every transaction specifies the ID of the shard it belongs to.
- A transaction belonging to a particular shard shows that it has occurred between two accounts which are native to that particular shard.
- Transaction group has transactions which belong to only that shard ID and are unique to it.
- Specifies the pre and post state root.
Now, let’s look at the top level aka the second level.
The Second Level
Image courtesy: Hackernoon.
No, don’t be scared! It is easier to understand than it looks.
There is the normal block chain, but now it contains two primary roots:
- The state root
- The transaction group root
The state root represents the entire state, and as we have seen before, the state is broken down into shards, which contain their own substates.
The transaction group root contains all the transaction groups inside that particular block.
Properties Of Level Two
- Level two is like a simple blockchain, which accepts transaction groups rather than transactions.
- Transaction group is valid only if:a) Pre state root matches the shard root in the global state.
b) The signatures in the transaction group are all validated. - If the transaction group gets in, then the global state root becomes the post-state root of that particular shard ID.
So how does cross-shard communication happen?
Now, remember our island analogy?
The shards are basically like islands. So how do these islands communicate with each other? Remember, the purpose of shards is to make lots of parallel transactions happen at the same time to increase performance. If Ethereum allows random cross shard communication, then that defeats the entire purpose of sharding.
So what protocol needs to be followed for cross-shard communication?
Ethereum chose to follow the receipt paradigm for cross-shard communications. Check this out:
Image courtesy: hackernoon
As you can see here, each individual receipt of any transaction can be easily accessed via multiple Merkle trees from the transaction group Merkle root. Every transaction in a shard will do two things:
- Change the state of the shard it belongs to
- Generate a receipt
Here is another interesting piece of information. The receipts are stored in a distributed shared memory, which can be seen by other shards but not modified. Hence, the cross-shard communication can happen via the receipts like this:
Image courtesy: Hackernoon
What are the challenges of implementing sharding?
- There needs to be a mechanism to know which node implements which shard. This needs to be done in a secure and efficient way to ensure parallelization and security.
- Proof of stake needs to be implemented first to make sharding easier according to Vlad Zamfir. In a proof-of-work system it will be easier to attack shards with lesser hashrate.
- The nodes work on a trustless system, meaning node A doesn’t trust node B and they should both come to a consensus regardless of that trust. So, if one particular transaction is broken up into shards and distributed to node A and node B, node A will have to come up with some sort of proof mechanism that they have finished work on their part of the shard.
Off-Chain State Channels
What is a state channel?
A state channel is a two-way communication channel between participants which enable them to conduct interactions, which would normally occur on the blockchain, off the blockchain. What this will do is that it will decrease transaction time exponentially since you are no longer dependent on a third party like a miner to valid your transaction.
So what are the requirements to do an off-chain state channel?
- A segment of the blockchain state is locked via multi-signature or some sort of smart contract, which is agreed upon by a set of participants.
- The participants interact with each other by signing transactions among each other without letting submitting anything to the miners.
- The entire transaction set is then added to the blockchain.
The state channels can be closed at a point which is predetermined by the participants according to Slock.it founder Stephan Thual. It could either be:
- Time lapsed eg. the participants can agree to open a state channel and close it after 2 hours.
- It could be based on the total amount of transactions done eg. close the chain after $100 worth of transactions have taken place.
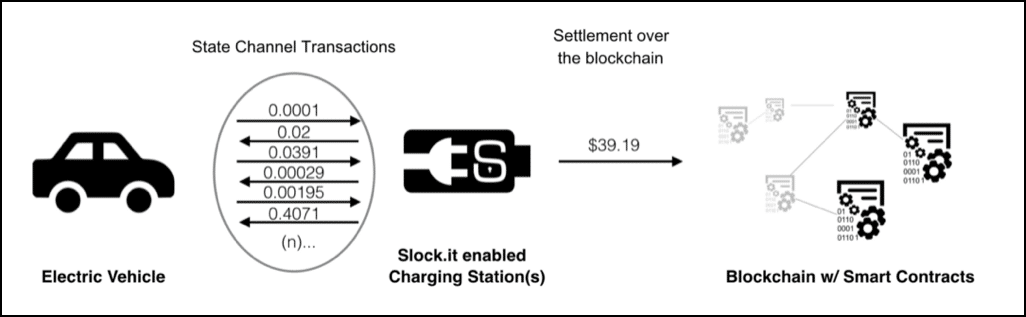
Image Courtesy: Stephan Tual Medium Article
So, in the image above. We have a car which directly interacts with the charger and does a total of $39.19 worth of transactions. Finally, after a series of interactions the entire transaction chunk is added to the blockchain. Imagine how much time it would have taken if they had to run every single transaction through the blockchain!
The off-chain state channel that bitcoin is looking to implement is the lightning network.
What is the lightning network?
The lightning netwok is an off-chain micropayment system which is deigned to make transactions work faster in the blockchain. It was conceptualized by Joseph Poon and Tadge Dryja in their white paper which aimed to solve the block size limit and the transaction delay issues. It operates on top of Bitcoin and is often referred to as “Layer 2”. As Jimmy Song notes in his medium article:
“The Lightning Network works by creating a double-signed transaction. That is, we have a new check that requires both parties to sign for it to be valid. The check specifies how much is being sent from one party to another. As new micro-payments are made from one party to the other, the amount on the check is changed and both parties sign the result.”
The network will enable Alice and Bob to transact with each other without the being held captive by a third part aka the miner. In order to activate this, the transaction needs to be signed off by both Alice and Bob before it is broadcasted into the network. This double signing is critical in order for the transaction to go through.
However, here is where we face another problem.
Since the double check relies heavily upon the transaction identifier, if for some reason the identifier is changed, this will cause an error in the system and the Lightning Network will not activate. In case, you are wondering what the transaction identifier is, it is the transaction name aka the hash of the input and output transactions.
This is the transaction identifier.
A bug called “Transaction Malleability” can cause the transaction identifier to change. However, this will not be a problem anymore, because Segwit activation removes this bug.
Ethereum is also planning to activate something like the lightning network which is called “Raiden”.
Plasma
Plasma along with lightning network/Raiden will introduce a whole new layer to the Ethereum architecture:
Image courtesy: Medium.
Plasma is a series of contracts that run on top of the root chain (the main Ethereum blockchain). If one were to envision the architecture and the structure, then think of the main blockchain and the plasma blockchains as a tree. The main blockchain is the root while the plasma chain aka child blockchains are the branches.
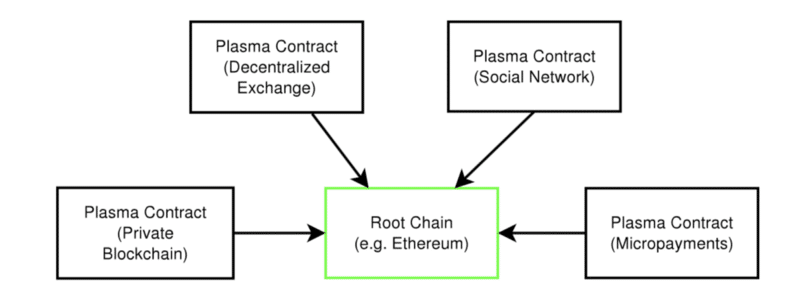
This greatly reduces the load on the main chain. Periodically the branches keep sending reports to the main chain. In fact, you can view the Root Chain as the supreme court and all the branches as the subordinate courts which derives its powers from the main court.
All the branch chains can issue their own unique tokens which can incentivize chain-validators to take care of the chains and to ensure that it is fault-free. Each branch has its own independent data and when it does need to submit some data to the main chain, it doesn’t dump all its contents, it just submits the blog header hash to the main chain.
Not only does plasma save up a lot of space in the main chain, it also increases the transaction process speed exponentially. If implemented properly, this could be one of the most revolutionary changes ever made to Ethereum and cryptocurrency in general.
Looking Ahead
Cryptocurrency, and especially, bitcoin and ethereum are becoming more and more mainstream. In order to keep pace with the increased usage, they need to seriously step it up when it comes to scalability. Fortunately, there are some fascinating solutions which could give them some very interesting results. Can they truly solve the scalability issue though? That remains to be seen.
What is Ethereum Metropolis: The Ultimate Guide
Metropolis is upon us! Or at least it’s the first iteration. After a lot of deliberations and updates, the time has finally arrived for the next big jump. There is a lot of buzz going on right now and for good reason. The last time Ethereum did a network shift i.e. from Frontier to Homestead, the price jumped more than 100% from $12 to $30.
Image courtesy: Wealth Daily
So is the price of Ether going to go up?
What are the features that metropolis is going to bring into Ethereum?
Since Ethereum needs to do a hard-fork to get into Metropolis, will it create another new coin? Will we have 3 Ethereum coins (along with ETC and ETH)?
Let’s find that out in this guide.
What is Ethereum Metropolis? The 4 Stages of Ethereum.
This, not the first time Ethereum has upgraded of course and it won’t be the last time. Ethereum was not designed to be just a mode of currency. It was designed to be a platform for decentralized applications. However, before it can do so, it needs to go through various stages of growth. With each stage, Ethereum “levels up” by incorporating more and more properties making its system more robust and seamless.
The complete launch process of Ethereum was divided into 4 stages. This was done to make sure that various phases got their own developmental time and that every stage was developed as efficiently and optimally as possible.
The 4 stages are as follows:
- Frontier: This was what everyone got when Ethereum was first launched.
- Homestead: The stage that we are on as of writing.
- Metropolis: The upcoming phase.
- Serenity: The final stage.
Metropolis is the 3rd stage in the 4-stage process and there are a lot of interesting features that are coming as and when it gets implemented. Here are some of the main ones which are going to have plenty of repercussions.
- Zk-Snarks.
- Proof of Stake early implementation.
- Flexibility and robustness of smart contracts.
- Account Abstraction.
Let’s go through each and every one of them one-by-one.
Feature #1: Zk-Snarks
One of the biggest and most important features that Metropolis is bringing along is the implementation of Zk-Snarks. Zk-Snarks stands for “Zero-Knowledge Succinct Non-Interactive Argument of Knowledge”. Zk-Snarks is based on zero knowledge proof.
What is Zero Knowledge Proof?
There are two parties when it comes to a zero-knowledge proof (as stated above), the prover and the verifier. Zero knowledge states that a prover can prove to the verifier that they possess a certain knowledge without telling them what that knowledge actually is
Properties of a zero knowledge proof (ZKP)
For a ZKP to work it needs to satisfy certain parameters:
- Completeness: If the statement is true then an honest verifier can be convinced of it by an honest prover.
- Soundness: If the prover is dishonest, they can’t convince the verifier of the soundness of the statement by lying.
- Zero-Knowledge: If the statement is true, the verifier will have no idea what the statement actually is.
So now that we have a basic idea of what a zero-knowledge proof is, let’s checkout an example of it before we dive deep into zk-snarks and its application in the blockchain.
Zero-Knowledge Sudoku
For those who don’t know, Sudoku is a Japanese puzzle where you get a 9X9 table which looks something like this:
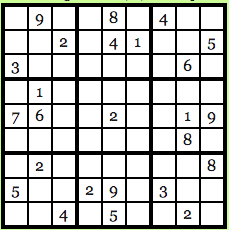
Image courtesy: Computational Complexity Blog.
The idea is to fill up every row, every column and every 3X3 block with numbers from 1-9 and no number should repeat itself. So, the solution for the puzzle above looks like this:
Image courtesy: Computational Complexity Blog.
As you can see, every row, column, and 3X3 block is unique and not a single number has been repeated. Let’s go back to our old friends Anna and Carl. Anna has found the solution to the Sudoku puzzle and Carl, skeptic that he is, doesn’t believe her and wants Anna to prove that she does indeed know the solution. Anna wants to prove her honesty, but at the same time, she doesn’t want Carl to know the exact solution of the puzzle. How will she go about it? Anna is going to use Zero Knowledge to prove the validity of her claim.
Firstly, Carl will run the Sudoku solution through a computer program which has been verified, to be honest, and the program will run the numbers through a randomly chosen substitution cipher. Say, for this particular problem the cipher that the program has chosen is this:
The chosen program and cipher is such that each digit has the same chance of being transmuted into its substitution as any other number. Basically, 1 has as much chance of being transmuted as 3 and 4 has as much chance of being transmuted as 9 and so on and so forth. So, using this cipher gives us the following solution to the puzzle above:
Image courtesy: Computational Complexity Blog.
Anna gets the transmuted solution now, keep in mind that Carl still doesn’t know what the original solution was and he doesn’t possess the transmuted solution either. So, what Anna does now is that she hides all the numbers in the puzzle by using a “lockbox mechanism”, basically Carl won’t be able to see any of the numbers and will see an empty 9X9 grid in front of him.
Carl now has 28 choices in front of him:
- Reveal a row.
- Reveal a column.
- Reveal a 3X3 box.
- Reveal the transmuted version of the original puzzle.
Suppose Carl wants to know what the third row looks like:
Image courtesy: Computational Complexity Blog.
This is what he will see. Carl will see that every number in the row is unique and since every possible number in the original solution had the same probability of being transmuted via the cipher, Carl will have no clue as to what the original solution is.
Now suppose, Carl decides to take the last option and wants to see what the original puzzle in looks like when transmuted:

Image courtesy: Computational Complexity Blog.
Once again, since the cipher was chosen at random and all the numbers have the same probability of being transmuted, Carl will have no idea what the original solution is. Carl can now go through all 28 of his choices and eventually he will be satisfied with the validity of Anna’s statement.
Why?
Because, if Anna was indeed cheating, there is no way that she could have found a cipher to give unique solutions for all 28 of Carl’s choices. If Carl just chooses one option, Anna’s chances of getting away with cheating are 27/28. BUT if Carl chose to do random test multiple times, suppose he chooses to test it 150 times, Anna’s choice of getting away with cheating drops down to (27/28) ^150 which is < 0.5%.
So, let’s check out the zero-knowledge properties of this scenario:
- Completeness: The cipher program being used has been verified, to be honest, and both Anna and Carl are following protocol.
- Soundness: If Carl does random tests 150 times, Anna’s chances of getting away with cheating is < 0.5%.
- Zero-Knowledge: Anna never had to reveal to Carl what the original solution was.
So, that’s how zero knowledge works in the “real world”. How do we implement zero knowledge in code via zk-snarks and what is its use in the blockchain?
What is the use of Zk-Snarks?
Zk-Snarks stands for “Zero-Knowledge Succinct Non-Interactive Argument of Knowledge”. Its use in modern blockchain technology is immense. To understand its application, it is important to know how a smart contract works. A smart contract is basically an escrow of funds which gets activated once a particular function is done.
Eg. Anna puts 100 ETH in a smart contract that she gets into with Carl. Carl has to do a particular task, on the completion of which, Carl will get the 100 ETH from the smart contract.
This gets complicated when then tasks that Carl has to do are multi-layered and confidential. Suppose you have entered a smart contract with Anna. Now, you will only get the payment if you do A, B and C. What if you don’t want to reveal the details of A, B and C because they are confidential to your company and you don’t want any competitors to know what you have to do?
What Zk-Snarks does is that it proves that those steps have been taken in the smart contract without revealing what those steps actually are. It is very useful is protecting you and your company’s privacy. It can just reveal part of the process without showing the whole process itself and prove that you are being honest about your claims.
How does a Zk-Snark work
A Zk-Snark consists of 3 algorithms: G, P and V.
G is a key generator takes an input “lambda” (which must be kept confidential and shouldn’t be revealed under any circumstances) and a program C. It then proceeds to generate two publicly available keys, a proving key pk, and a verification key vk. These keys are both public and available to any of the concerned parties.
P is the prover who is going to use 3 items as input. The proving key pk, the random input x, which is publicly available, and the privacy statement that they want to prove the knowledge of without revealing what it actually is. Let’s call that private statement “w”. The P algorithm generates a proof prf such that: prf = P(pk, x,w).
The verifier algorithm V has basically returned a boolean variable. A Boolean variable has only two choices, it can be TRUE or it can be FALSE. So, the verifier takes in the verifying key, public input x and proof prf as input such as:
V(vk,x,prf)
..and returns TRUE if the prover is correct and false otherwise.
Now, about the parameter lambda. The value of the “Lambda” must be kept confidential because then anyone can use it to generate fake proofs. These fake proofs will return a value of TRUE regardless of whether the prover actually has knowledge of private statement “w” or not.
Functionality of Zk-Snark
For showing the functionality of a Zk-Snark we are going to use the same example function that Christian Lundkvist used in his article for Consensys.
This is what the example program looks like:
function C(x, w){return ( sha256(w) == x );}
Basically, the function C takes in 2 values as input, a public hash value “x” and the secret statement that needs to be verified “w”. If the SHA-256 hash value of w equals “x” then the function returns TRUE otherwise it returns FALSE. (SHA-256 is the hash function that is used in Bitcoin).
Let’s bring back our old friends Anna and Carl for this example. Anna being the prover and Carl the skeptic is the verifier.
The first thing that Carl, as the verifier, has to do is to generate the proving and verifying key using the generator G. For this, Carl needs to generate the random value “lambda”. As stated above, however, he needs to be super careful with Lambda because he can’t let Anna know its value to stop her from creating fake proofs.
Anyway, this is what that will look like:
G(C, lambda) = (pk , vk).
Now that the two keys are generated, Anna needs to prove the validity of the statement by generating the proof. She is going to generate the proof using the proving algorithm P. She is going to prove that she knows the secret value “w” which hashes (on parsing through SHA-256) to give the output x. So, the proving algorithm for proof generation looks like this:
prf = P( pk, x, w).
Now that she has generated the proof “prf”, she is going to give the value to Carl who is finally going to run the verification algorithm of Zk-Snarks.
This is what that will look like:
V( vk, x, prf).
Here, vk is the verifying key and x is the known hash value and prf is the proof that he has gotten from Anna. If this algorithm returns TRUE then this is means that Anna was honest and she indeed had the secret value “w”. If it returns FALSE then this means that Anna was lying about knowing what “w” is.
Zk-Snark and Ethereum
Ethereum has been closely working with ZCash (Zero Cash, the cryptocurrency completely based on Zk-Snarks). If there is anyone who can show them how to incorporate zk-snarks on the blockchain it’s them. We, personally, cannot wait to see how Metropolis will be incorporating Zk-Snarks.
Feature #2: Proof Of Stake Early Implementation
So what is the difference between proof of stake and proof of work?
- Proof of work: This is the protocol that most cryptocurrencies like Ethereum and Bitcoin have been following so far. This means that miners “mine” cryptocurrencies by solving crypto-puzzles using dedicated hardware.
- Proof of stake: This protocol will make the entire mining process virtual. In this system, we have validators instead of miners. The way it works is that as a validator, you will first have to lock up some of your ether as stake. After doing that you will then start validating blocks which basically means that if you see any blocks that you think can be appended to the blockchain, you can validate it by placing a bet on it. When and if, the block gets appended, you will get a reward proportional to the stake you have invested. If, however, you bet on the wrong or the malicious block, the stake that you have invested will be taken away from you.
To implement “proof of stake” Ethereum is going to use the Casper consensus algorithm. In the beginning, it is going to be a hybrid style system where the majority of the transactions will still be done proof of work style while every 100th transaction is going to be proof of stake. What this will do is that it will provide a real-world test for proof of stake on Ethereum’s platform. But what does that mean for Ethereum and what are the advantages of this protocol? Let’s take a look.
Advantages of proof of stake
- Lowers the overall energy and monetary cost: The world’s bitcoin miners spend around $50,000 per hour on electricity. That’s $1.2 million per day, $36 million per month and ~$450 million per year! Just put your head around those numbers and the amount of power being wasted. By using “Proof-of-stake” you are the making the whole process completely virtual and cutting off all these costs.
- No ASIC advantage: Since the whole process will be virtual, it wouldn’t depend on who has the better equipment or ASICs (application-specific integrated circuit).
- Makes 51% attack harder: 51% attack happens when a group of miners gain more than 50% of the world’s hashing power. Using proof of stake negates this attack.
- Malicious-free validators: Any validator who has their funds locked up in the blockchain would make sure that they are not adding any wrong or malicious blocks to the chain, because that would mean their entire stake invested would be taken away from them.
- Block creation: Makes the creation of newer blocks and the entire process faster. (More on this in the next section).
- Scalability: Makes the blockchain scalable by introducing the concept of “sharding” (More on this later.)
Even though there have been various simplistic implementations of Proof of Stake before, what separates Casper from the rest is that it incentivizes the honest miners and punishes the dishonest ones. If you have put your stake on a malicious block, then the stake will be taken away from you. It will punish anyone who doesn’t play by the rules.
This is how Vitalik explains it:
“Imagine 100 people sitting around a circular table. One person has a bundle of papers, each with a different transaction history. The first participant picks up a pen and signs one, then passes it onto the next person, who makes a similar choice. Each participant only gets $1 if they sign the transaction history that most of the participants sign in the end. If you sign one page and later sign a different page, your house burns down,”
He then added that this is probably a good incentive to sign the right piece of paper!
- What is the difficulty time bomb?
- What is there to incentivize the miners to move from a proof-of-work protocol to a proof-of-stake protocol?
Miners buy thousands of dollars’ worth of equipment so that they can mine for blocks. The moment POS comes on board; all that equipment becomes worthless. Imagine spending so much money and having super intricate pools set up, and all that becoming completely useless.
If that is the case, then what is there to stop the miners from staying on the old proof-of-work chain and continue mining on it? This will, in essence, create three Ethereum coins: Ethereum Classic, Ethereum Proof-of-work and Ethereum Proof-of-stake. That is going to be an absolute nightmare.
Not only will that greatly decrease the economic value and credibility of Ethereum, it is also going to dilute the hashrate of the overall chain which can make it vulnerable to hacker attacks.
In order to make sure that there is the proper incentive to miners to join the new chain, the Ethereum developers introduced the difficulty time bomb. The time bomb was introduced on 7th September 2015. To understand how the difficulty time bomb works, it is important to understand how difficulty and mining works.
What is difficulty and how does it work?
The concept of difficulty started with bitcoin. When bitcoin was first introduced, mining was extremely simple and anybody could do it using their PC. However, as bitcoin got more and more popular the number of miners on the network increased. This raised a very real possibility of miners going out of control and mining out all the remaining bitcoins in the space of a year. Satoshi Nakamoto envisioned this happening and hence introduced the “difficulty” system.
The difficulty system works like this: Miners spend their computational power to solve cryptographic puzzles. The way they do that is that they randomly append a random string (called nonce) to the hash of the block and then they hash the whole string. If the resulting number is less than a particular fixed number, then it is considered to be successful and the new block is added to the blockchain. Finding this “nonce” is extremely difficult and random and that is the heart of all mining.
If we were to recap the whole process then this is what it would look like:
- The hash of the contents of the new block is taken.
- A nonce (random string) is appended to the hash.
- The new string is hashed again.
- The final hash is then compared to the difficulty level and see whether it’s actually less than that or not.
- If not, then the nonce is changed and the process repeats again.
- If yes, then the block is added to the chain and the public ledger is updated and alerted of the addition.
- The miners responsible for this given the block reward.
The difficulty is adjusted every 2016th block.
The difficulty level is directly proportional to the rate at which the blocks are being mined. Bitcoin has an average block time of 10 seconds.
If the block time goes below that, then the difficulty level is increased, if it goes up, then the difficulty time decreases. This is done to make sure that the block time of bitcoin stays ~10 seconds.
This is basically how bitcoin mining works and Ethereum follows the same protocol as well.
So what will the difficulty time bomb do?
The difficulty bomb will exponentially increase the difficulty so much so that mining will become impossible.
Like we have said before, the difficulty level adjusts according to the rate at which the blocks are being mined. The Ethereum difficulty adjustment algorithm looks like this:
block_diff = parent_diff + parent_diff // 2048 * max(1 – (block_timestamp – parent_timestamp) // 10, -99) + int(2**((block.number // 100000) – 2))(In here “//” is the division operator such that 6//2 = 3 and 9//2 = 4.)
So, let’s understand what that basically means in plain English:
Block_timestap = the time at which the block was mined.
Parent_timestamp = the time at which the parent block aka the block before this was mined.
- If (block_timestamp – parent_timestamp) < 10 seconds then a factor of “parent_diff // 2048 * 1” is added to the difficulty.
- If (block_timestamp – parent_timestamp) is between 10-19 seconds then the difficulty is kept the same.
- If (block_timestamp – parent_timestamp) > 20 seconds then the difficulty is reduced by “parent_diff // 2048 * -1” to a maximum of “parent_diff // 2048 * -99”.
This is how the difficulty adjustment algorithm worked in the Homestead version of Ethereum. The idea is to keep the block time ~15 seconds.
So, what the difficulty bomb is going to do is that it will increase the difficulty by such an exponential amount without adjusting it that it will take more and more time to solve the cryptographic puzzles. Eventually, it will become near impossible to mine on the chain. This phenomenon is called the “Ethereum Ice Age”, the time all mining POW style becomes impossible.
When this happens, the miners will have no option BUT to go the new Ethereum chain which has Proof-Of-Stake on it.
Will this be utilized in Metropolis?
The difficulty time bomb is supposed to explode at the end of 2017 but it looks like it has been delayed by a year and a half. However, with Metropolis, the development team has made two changes that will smooth the process over to POS.
- Casper will be applied and as mentioned above, every 100th block will be mined via proof of stake.
- The mining reward is going to decrease from 5 ether to 3 ether.
The goal is to get the entire network used to Proof of Stake protocol and to iron out all the issues before fully utilizing it in Serenity.
Feature #3: Robustness and Flexibility of Smart Contracts
What are smart contracts?
It won’t be an exaggeration to say that Smart Contracts are the lifeblood of ethereum.
Smart contracts are how things get done on ethereum. The idea is simple. Imagine A and B getting a transaction or a function done without the intervention of a third party. Suppose A tells B to do a task for which B charges 1 ETH. A puts that 1 ETH in a “box”. If B does the task then that 1 ETH goes to B, if he doesn’t then that 1 ETH goes back to A. The “box” in this analogy is a smart contract. This is a rough analogy to help you understand how it works.
So, what are the innovations that Ethereum is bringing along to make their smart contracts better and more easy to develop?
Let’s understand how things function in Ethereum.
Suppose A gives B a smart contract to execute. Each and every function in that contract requires the use of certain computational power on B’s side. This computational power is called “gas”. The money required to pay up for this gas is called “ether”. The gas price chart looks like this:
Image courtesy: Etherscan
Now, while bitcoin usually spends the same computational power for all transactions, Ethereum can vary the computational power required for each of its contracts. Each contract has its own gas limit which is set by the contract giver. This can lead to two scenarios:
- The gas required is more than the limit set. If that’s the case then the state of contract is reverted back to its original state and all the gas is used up.
- The gas required is less than the limit set. If that’s the case, then the contract is completed and the leftover gas is given over to the contract setter.
During a contract execution if one wishes to go back to an earlier state during the execution, it would require manual triggering of an exception eg. if one were to cancel a transaction then they will have to double spend to stop it from going through. In order to revert a contract back to its original state developers use the “throw” function. While the throw function does help the contract’s state to go back to the previous one, it eats up all the gas in the contract.
To counter this problem, Metropolis is beefing up the “revert” function to help the contracts go back to the previous state without eating up all the gas. The unused gas will be refunded to the contract creator. Along with the revert function, Metropolis is introducing the “returndata” opcode which will enable contracts to return variable sized values.
Feature #4: Account Abstraction
Before we get into what account abstraction means, let’s understand what abstraction means. Abstraction means that anyone can use any system or protocol without completely knowing the ins and outs and all the technical details. Eg. When you use your iPhone, you don’t need to be a programmer or an engineer to operate it. You simply press on the screen to activate an app, or press on the call button to call someone. You don’t need to know how pressing certain apps activates the circuit inside the phone or how certain apps were programmed. Abstraction makes a complex technology accessible to the masses by removing the complexities.
Abstraction is what Ethereum plans to achieve in the future. In a hypothetical decentralized future, they envision everyone to use DAPPS without even realizing that they using a DAPP based on Ethereum. They basically want Ethereum to “disappear” in the background. Metropolis is taking a major step towards doing just that by introducing “Account Abstraction”.
As part of abstraction, Ethereum is planning to blur the line between its two accounts. Ethereum, as of writing at least, has two accounts. One is the external account, the one controlled by keys that most users are aware of i.e. wallet accounts. Then you also have the contract account aka the smart contract code in the blockchain. The idea is to essentially allow users to define their external accounts in the form of a smart contract.
Once this is done, the codes backing the keys can put their own unique spin on the transactions backing the code. How does that help? As you may be aware that Quantum computing is fast becoming a possible threat to the cryptography which makes the cryptocurrencies. So suppose you want to save your transactions from a quantum attack by a malicious attacker, what can you do about it?
With account abstraction, you can use signature schemes like hash ladders to define your own account which has a possibility of being quantum proof. Your accounts can now be customizable quite like a smart contract.
What are Byzantium and Constantinople?
The terms “Byzamtium” and “Constantinople” is being thrown all around in the cryptosphere. What do they mean? Metropolis is bringing in a lot of significant changes at the same time. It won’t be possible to bring in all these changes at one go and not overwhelm the users and the developers. This is why, Ethereum is launching Metropolis in two phases and both will be introduced as hardforks.
These two phases are:
- Byzantium.
- Constantinople.
After a lot of delays, Byzantium hardfork will now occur at block number 437,000,000, or about October 17 given current block production metrics.
Byzantium will introduce a lot of features. The main ones being:
- Zk-Snarks.
- Revert and returndata.
- Account abstraction.
It is not clear when Constantinople will happen but it is being planned to take place in 2018. The main feature of it is to smooth out all the issues that may come up because of Byzantium and, more importantly, to introduce the proof-of-stake and proof-of-work hybrid chain.
So Ethereum is going to hard fork again? Will there be a third ethereum coin?
No, there won’t be.
Because of the Ethereum-Ethereum Classic and the Bitcoin-Bitcoin Cash hardforks, people have started to assume that all hard forks are bound to cause chain splits. That is simply not the case.
The reason why those forks split the chain was because the changes proposed (the ethereum hardfork and the Segwit activation) were so controversial that not everyone was on board.
However, these upgrades have been unanimously agreed upon for a long time. Everybody knew that this was going to happen. This hardfork is not the result of an emergency, this hardfork is the result of an upgrade, which is why there won’t be any community split and there won’t be a new coin.
The only bone of contention could be the proof-of-stake hardfork, however, the miners are not going to gain much by remaining on the old chain since, as already discussed, the difficulty bomb will make mining near impossible.
Ethereum Metropolis Conclusion: What is going to happen now?
So, is the value of ether going to go up?
We don’t know, we are not financial advisors. You need to do your own research before you invest in a coin. However, what we can say for sure is that they last time ethereum upgraded, the value went up >100%..
Byzantium is bringing in so many changes to Ethereum that it will be fascinating to see how things turn out. The implementation of zk-snarks is particularly game changing and of course, Constantinople with its proof of stake is going to be something that everyone in the crypto world is going to keep their eye on. The upcoming year could be absolutely revolutionary for Ethereum and their dream of a decentralized future.
Why Most ICO’s Will Fail: A Cold Hard Truth
In this guide you will learn why most ICO’s Will Fail..
On June 12, 2017, an Ethereum based called Bancor held its ICO. It raised $153 million in 3 hours. No, you are not reading it wrong, 153 million…..in 3 hours!!!
If that doesn’t get your brain melting, then how about this? The BAT ICO $35 million in 30 seconds!!! That’s near $1.2 million per second! And if that still doesn’t get your jaw dropping, then how about this? Have you heard of UET? UET had an ICO which raised $40,000 in just 3 days. Admirable if not particularly mind-blowing. Why do we bring it up after talking about Bancor and BAT?
Well, UET stands for “Useless Ethereum Token”, it is a “joke coin”.
Here is the sales pitch that they used, “UET is a standard ERC20 token, so you can hold it and transfer it. Other than that… nothing. Absolutely nothing.” And they raised $40,000 in 3 days! Welcome to the crazy world of ICOs! There is no doubt that ICOs have changes the financial landscape over the past 2 years. In the first half of 2017 alone they raised over $1 billion!
However, all these insane success stories tend to make us look at facts with rose-tinted glasses. The fact is, that around 99% of all ICOs out there will fail. And that’s not exaggerated doom and gloom, over the last few years, thousands of cryptocurrencies have been created and over 90% of them have failed. And the fact also remains that given the insane success of most ICO’s, scammers are flooding the market creating bogus dapps/coins to get their fill of the ICO pie and effectively create an “ICO bubble”.
So, keeping all this in mind let’s aim to answer this simple question: “Why are most of the ICOs going to fail?”
A quick disclaimer before we continue
Before we continue, we want to make something very clear. We don’t “hate” on ICOs. We believe that ICOs are truly revolutionary and will continue to evolve and will become an amazing vehicle for developers, entrepreneurs and investors who are looking to innovate and change the world by just showing their concept aka a whitepaper. (Well, we hope more than just a whitepaper) That’s truly brilliant.
With that being said, let’s start.
Why Most ICO’s Will Fail: A Cold Hard Truth
So, how does an ICO work?
Firstly, the developer issues a limited amount of tokens. By keeping a limited amount of tokens they are ensuring that the tokens itself have a value and the ICO has a goal to aim for. The tokens can either have a static pre-determined price or it may increase or decrease depending on how the crowd sale is going.
Tokens are basically native currencies that can be used in an environment (think of the arcade coins that you needed to play games in an arcade) or they give their owners various rights inside the native environment (Think of the wristbands that certain nightclubs use which entitles you to get a certain number of free drinks).
The transaction is a pretty simple one. If someone wants to buy the tokens they send a particular amount of ether to the crowd-sale address. When the contract acknowledges that this transaction is done, they receive their corresponding amount of tokens.
So, that’s a general idea on how ICOs works. But then why do most ICOs fail. The reason why most ICOs fail is that most developers/entrepreneurs do not pay any attention to the three pillars that make an ICO:
- Cryptoeconomics.
- Utility.
- Security.
Pillar #1: Cryptoeconomics
It is funny how most developers forget the “cryptoeconomics” of their ICOs. There are two words that makeup cryptoeconomics: “cryptography” and “economics”. While most developers pay attention to the cryptography part, they hardly pay any attention to the “economics” part. As a result of which, it is very rare to find a token whose economic skeleton has been properly and thoroughly mapped out.
In order for the token to be decently valuable in the long run, there must be sufficient demand for it but that is not what is usually seen in the ICOs. What is seen is unsustainable token inflation which largely happens because of flawed economic models and the greater fool theory (more on that in a bit).
For these permanently inflationary tokens, their demand must always outpace their inflation for them to be valuable in the long run, which more often than not creates a Ponzi Scheme like scenario.
Before we go into all that, however, we need to understand where the fundamental problem of most ICO economic model lies.
One of the biggest advantages of ICOs is that anyone can come and raise money for their concept…not a finished product, a concept. There is still a long way to go before that concept can become a product and as with anything, there is a 90-95% chance that it will be a failure.
However, many of the early adopters of ICOs have made a killing because of the low entry and the high profit. As a result of this everyone else developed a massive case of FOMO (Fear Of Missing Out) and started pouring millions into concepts that didn’t even have an alpha version ready. Look at this, for instance, ICOs made nearly $800 million in the second quarter of 2017 alone! Compared to that, Venture capital made just $235 million:
These are people who have little to no idea about how the blockchain works, they are just putting in money to make a quick buck. Seeing this trend, the developers shifted their focus. Instead of making Dapps/currencies which added something new and unique to the ecosystem, they started making products for the ICO.
Their end goal became: “Build a flashy enough whitepaper to get good money in ICOs”. Because of this rampant speculation and very little due diligence, the “Greater Fool Theory” came into play.
What is the Greater Fool Theory?
The Greater Fool Theory is an economic theory which states that the price of an object increases not because of the value that it brings in but because of the irrational beliefs attached to it. Art is a great example of the greater fool theory.
So let’s apply the same to ICOs. You have a bunch of dapps and currencies coming up which are bringing in nothing new to the ecosystem. However, because they have been hyped up so much and there so many ignorant investors around, their value increases anyway, and as a result, the tokens face an inflation.
So, let’s recap what we have learned so far:
- Investors are investing millions into concepts that don’t even have an alpha version of their product.
- Investors are desperate to put their money in because they think that ICOs are a way to get rich quick.
- In order to cash in on this, developers are creating products more aimed towards ICOs than to give actual value.
- Because of the “Greater Fool Theory.” the value of the tokens gets inflated.
If this sounds suspiciously like a bubble then yes, you are right and the thing is, we have been here before, we have seen this play out. The whole ICO situation is scarily reminiscent of another wave that swept us in the late 90’s. They say that those who are not aware of history are bound to repeat it. So let’s do a quick history lesson and turn back the clocks.
The Dot-Com Bubble
Around 1997, the internet became big and tech companies began to emerge everywhere. Investors started putting in their money and flipping their investments into huge sums. Eventually, everyone who saw this started getting major FOMO (fear of missing out) and they began giving away their money to companies without even having any idea as to whether the business had the potential to work or not.
Common sense went out of the window and every random internet business was making a killing in the IPOs. Warren Buffet noted that:
“The fact is that a bubble market has allowed the creation of bubble companies, entities designed more with an eye to making money off investors rather than for them. Too often, an IPO, not profits, was the primary goal of a company’s promoters.”
BOOM!
He hit the nail right on the head, most of the companies that got millions from their investors failed and some turned out to be nothing more than scams. Eventually, the bubble burst in 2002. Companies crashed and lost millions within a year. One of the most infamous examples of this is Pets.Com which lost $300 million in just 268 days!
The parallels between the ICO bubble and the dot-com bubble are a bit frightening. Much like dot-coms, the ICOs have attracted a lot of investors who don’t want to miss out on the gold rush. Much like the dot-coms ALL the investing is done purely from speculation. You have to realize that most of the companies that you are investing in, in ICOs barely have anything ready. Most of them don’t have the alpha version of their end result, it is all based on speculation and the potential of the project.
As with anything, most of these projects will fail to get the end results. The reason why the Ethereum ICO worked so wonderfully was that it had a dedicated and driven team of talented developers who were a day in and day out to make it a success, same with Golem.
The parallels are very apparent and it can get real scary thinking about it. But we are not market experts. All we can do is speculate. We don’t know whether we are living in the “ICO bubble” or not, nor do we know whether it is a bubble that is going to pop.
What we do know is that unless developers stop with their “get rich quick schemes” and actually pay attention to launching ICOs which bring in true value and has a concrete economical skeleton, then we will be seeing patterns which are depressingly similar.
Pillar #2: Utility
What is the definition of Utility? Utility means the total satisfaction that is received by the consumption of the goods or services. Most of the ICOs do not maximize their token utility. The tokens should be absolutely integral to the ICO and must increase the overall value of your final product.
If you are an ICO developer, then ask yourself this question: If you take away your token does your business fall apart? If the answer is no, then you don’t need a token. There are only a few cases that make sense to tokenize. Most people get tokens only so they can “HODL” it and buy more bitcoin and ethereum in the future! Is that all that your tokens are worth?
If you do use tokens for your business, then you need to completely understand its role and maximize its utility. You have to understand that tokens can be multi-purpose tools which can bring in a lot of “oomph” to your business. Your business model should be such that you are exploiting your tokens to the maximum possible limit.
(Before we continue, we would like to give shoutouts to the inimitable William Mougayar and Kyle Samani for their brilliant work and research.)
As William Mougayar points out in his Medium article, there are three tenets to token utility and they are:
- Role.
- Features.
- Purpose.
These three are locked up in a triangle and they look like this:
Each token role has its own set of features and purpose which are detailed in the following table:
Let’s examine each of the roles that a token can take up:
- Right
By taking possession of a particular token, the holder gets a certain amount of rights within the ecosystem. Eg. by having DAO coins in your possession, you could have had voting rights inside the DAO to decide which projects get funding and which don’t.
- Value Exchange
The tokens create an internal economic system within the confines of the project itself. The tokens can help the buyers and sellers trade value within the ecosystem. This helps people gain rewards upon completion of particular tasks. This creation and maintenance of individual, internal economies is one of the most important tasks of Tokens.
- Toll
It can also act as a toll gateway in order for you to use certain functionalities of a particular system. Eg. in Golem, you need to have GNT (golem tokens) to gain access to the benefits of the Golem supercomputer.
- Function
The token can also enable the holders to enrich the user experience inside the confines of the particular environment. Eg. In Brave (a web browser), holders of BAT (tokens used in Brave) will get the rights to enrich customer experience by using their tokens to add advertisements or other attention based services on the Brave platform.
- Currency
Can be used as a store of value which can be used to conduct transactions both inside and outside the given ecosystem.
- Earnings
Helps in an equitable distribution of profits or other related financial benefits among investors in a particular project.
So, how does this all help in token utility?
If you want to maximize the amount of utility that your token can provide then you need to tick off more than one of these properties. The more properties you can tick off, the more utility and value your token brings into your ecosystem. If the role of your tokens cannot be clearly explained, or if it doesn’t really tick off more than one of the roles given above, then your token doesn’t have any utility and you can do without it.
Now, let’s move onto another interesting concept called “Token Velocity”.
Token velocity in simple terms means: Are people going to hold on to the tokens for long-term gain or sell it off immediately? This is a problem with most ICO and token structures because they are being treated more as a vehicle for liquidation than as a store of long-term value. In fact, regarding this, Willy Woo did an interesting case study.
He plotted the performances of 118 coins, from the first day of their inception to the day he made the graph. His only qualification was this; the coin should have reached a market cap of at least $250,000 in any one year of its existence. Let’s see what he came up with:
Image courtesy: WooBull
See that red line soaring triumphantly over everyone else? That is bitcoin. It is the only crypto that has performed consistently and grown from strength to strength. (The blue line above the bitcoin line is a statistical aberration according to Woo).
In fact, Woo’s research becomes more interesting when you break it down even further. Here he has grouped the coins together according to the year of their inception. Let’s see how well the coins from each year group performed:
Image courtesy: WooBull
Yikes! That does not look good at all!
What this shows is that every year the coins are performing worse and worse. And the reason for that is simple. More and more scam ICOs are coming in and developers are not making valuable enough projects. As a result of which, we have tokens, which perform no other utility than being a means of liquidation and that is exactly why Bitcoin and Ethereum are so far and above everyone else. People realize their potential as a proper long-term store of values.
This is exactly why developers need to pay attention to token velocity. The reason why Bitcoin and Ethereum have such high values is because, they are low-velocity coins. Let’s quantify token velocity (TV):
Let’s quantify token velocity (TV):
TV = Total Trading Volume / Average Network Value.
So, more the trading volume aka more that coin is traded more the velocity. Consequently, less the network value, more the velocity.
Now if you examine this from the perspective of bitcoin, then you will know exactly why its velocity is less.
- No other crypto has as much network value as bitcoin.
- No one wants to trade off bitcoin because they know that there is value in holding it.
So, what should developers do to ensure that they have less token velocity? They need to work and re-examine their tokens. They need to understand whether a token is being fully utilized or not. They need to answer several questions, some of which are:
- Does my project really need a token?
- Am I fully exploiting the token and getting as much token utility as possible.
- Is my token useful only for initial liquidation purposes?
- Is there any value in holding my token long term?
- Is my token ticking off as many roles as possible?
It is only when developers work on the utility of their tokens will they be able to bring something which can contribute significantly to the ecosystem
Pillar #3: Security
And now we come to the third pillar… security
During your ICO and immediately after your ICO you have a big target on your back. If you haven’t paid attention to your security, hackers will attack you and they will rob you. In fact, this is what Chainanalysis had to say:
“More than 30,000 people have fallen prey to ethereum-related cyber crime, losing an average of $7,500 each, with ICOs amassing about $1.6 billion in proceeds in 2017.”
In fact, Chainanalysis claims that there is a 1 in 10 chance that you will end up a victim of the theft! That is staggering.
The crimes that happen largely fall into three categories:
- Faulty code.
- Phishing Schemes.
- Mismanagement of keys.
Faulty Code
Perhaps the most infamous example of this is the DAO attack.
The DAO aka the Decentralized Autonomous Organization was a complex smart contract which was going to revolutionize Ethereum forever. It was a decentralized venture capital fund which was going to fund all future DAPPS made in the eco-system.
The way it worked was pretty straightforward. If you wanted to have any say in the kind of DAPPS that would get funded, then you would have to buy “DAO Tokens” for a certain amount of Ether. The DAO tokens were indicators that you are now officially part of the DAO system and gave you voting rights.
If in case, you and a group of other people were not happy with the DAO then you could split from it by using the “Split Function”. Using this function, you would get back the ether you have invested and, if you so desired, you could even create your own “Child DAO”. In fact, you could split off with multiple DAO token holders and create your own Child DAO and start accepting proposals.
There was one condition in the contract, however, after splitting off from the DAO you would have to hold on to your ether for 28 days before you could spend them. And this was where the loophole was created. People saw this in advance and brought it up but the DAO creators assured that this was not going to be a big issue. They couldn’t have been more wrong.
The DAO Attack
On 17th June 2016, someone exploited this very loophole in the DAO and siphoned away one-third of the DAO’s funds. That’s around $50 million dollars. The loophole that the hacker(s) discovered was pretty straightforward in the hindsight.
If one wished to exit the DAO, then they can do so by sending in a request. The splitting function will then follow the following two steps:
- Give the user back his/her Ether in exchange of their DAO tokens.
- Register the transaction in the ledger and update the internal token balance.
What the hacker did was they made a recursive function in the request, so this is how the splitting function went:
- Take the DAO tokens from the user and give them the Ether requested.
- Before they could register the transaction, the recursive function made the code go back and transfer even more Ether for the same DAO tokens.
This went on and on until $50 million worth of Ether were taken out and stored in a Child DAO and as you would expect, pandemonium went through the entire Ethereum community. The price of Ether dropped from $20 to $13 overnight. This still remains the worst ICO hack ever. The aftermath of the hack was so extreme that it split Ethereum into two different currencies: Ethereum and Ethereum Classic.
Phishing Schemes
Here is something truly scary for you to wrap your head around.
Phishing scams have stolen up to $225 million in Ethereum related cybercrimes. In fact, as we have mentioned before, more than 30,000 people have fallen prey to ethereum-related cyber crime, losing an average of $7,500 each.
So, before we continue, what is phishing?
Phishing is the process by which scammers get your sensitive information (like credit card details) by impersonating someone trustworthy and of notable repute. The scammers usually use email and in some cases, they use social media. In fact, someone has been trying to phish ICO developers by impersonating our very own Ameer Rosic!
As a developer, you need to be very very very careful of this. Imagine giving away your card details or, more importantly, your key details just before your ICO! Obviously, the investors get scammed more than the developers. One of the more popular ways of scamming investors is by creating a fake social media profile which somewhat resembles the real ICO page and then manipulating potential investors to send money to their address.
Mismanagement Of Keys
If you are a developer, then there are 3 questions that you need to ask yourself:
- Where are you storing your private keys?
- How are you protecting your wallets?
- How are you protecting your customer’s tokens on your ecosystem?
- Who are you sharing your multi-sig wallet keys with?
If you are a developer, then one of the many doubts and fears that you will face from your investors is what is stopping you from running away with all of their funds? Which is a very valid question. The way that you can allay these fears is by using a multi-signature wallet.
What is a multi-signature wallet?
The easiest way of understanding how a multi-signature (multi-sig) wallet works like is by thinking of a safe which needs multiple keys to operate. A multi-signature wallet is great for 2 purposes:
- To create more security for your wallet and save yourself from human error.
- To create a more democratic wallet which can be used by one or more people.
How does multi-signature wallet save you from human error?
Let’s take the example of BitGo, one of the premier multi-sig wallet service providers in the world. They issue 3 private keys. One is held by the company itself, one is held by the user and the third one is a backup that the user can keep for themselves or give to someone trustworthy for safe keeping.
To do any sort of transaction in a BitGo wallet you will need at least 2/3 keys to operate. So even if you have a hacker behind you, it will super difficult for them to get their hands on 2 private keys. And on top of that, even if you lose your private key for whatever reason, you still have that backup key that you had given to your friend.
Now, how does a multi-signature wallet create a more democratic environment? Imagine that you are working in a company with 10 people and you need 8 approvals in order to make a transaction.
Using a software like Electrum you can simply create a custom multi-sig wallet with 10 keys. This way you can make seamless democratic transactions in your company. And that is exactly how you will allay fears regarding the safety of the investor’s money. Suppose you publicly declare that 5 of those keys will be given to neutral parties who are reputable members in the crypto environment that will obviously create more trust among the investors.
However, despite all this, even a multi-sig wallet is prone to a hack attack. A wallet is only as secure as the code that makes it. On July 19th, a vulnerability in the Parity Multsig wallet was exploited and hackers made do with $30 million in ether.
So next time you are about to hold an ICO please make sure that you are taking care of your security. No one wants to see a tweet like this:
Conclusion
ICOs are the “in thing” now and the number of ICOs held per month is increasing exponentially:
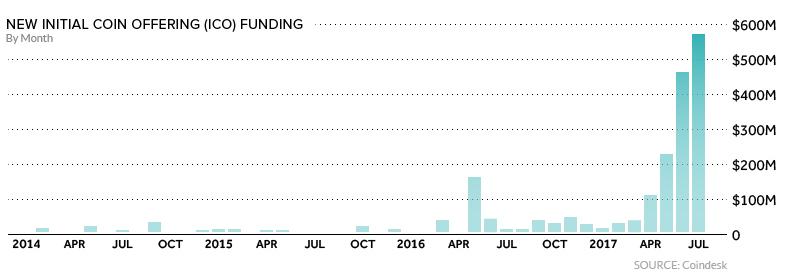
Image Courtesy: Investopedia
If you are a developer then, and there is no easy way of saying it, you will most likely fail to create an end product. Does this mean that we hate ICOs? We don’t. Like we said, we really think that it is revolutionary. But, if you are a developer then it is your responsibility to you, your potential investors, and to the future of cryptocurrency itself to use the ICOs as a means of creating something truly meaningful rather a method of making a lot of cash.
- Why are you doing your ICO?
- Is your token something that will bring genuine value?
- Are you sure you are not doing this just to make a quick buck?
If you cannot convincingly answer any of these questions then please, do not do your ICO. Don’t contribute to this “bubble”. Make something meaningful. Make something that will add to the environment, not exploit it.
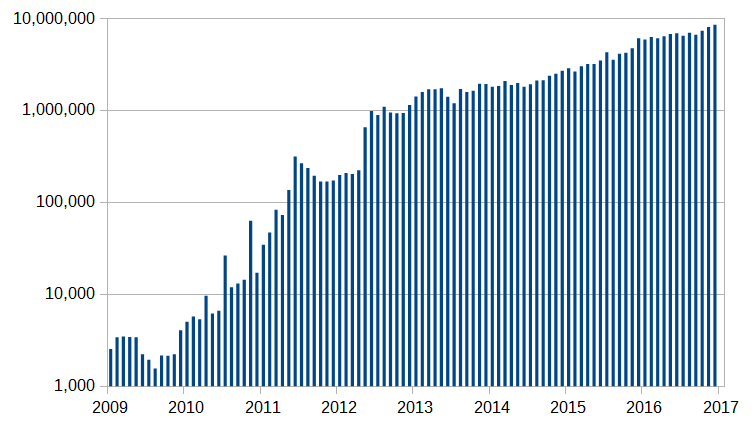
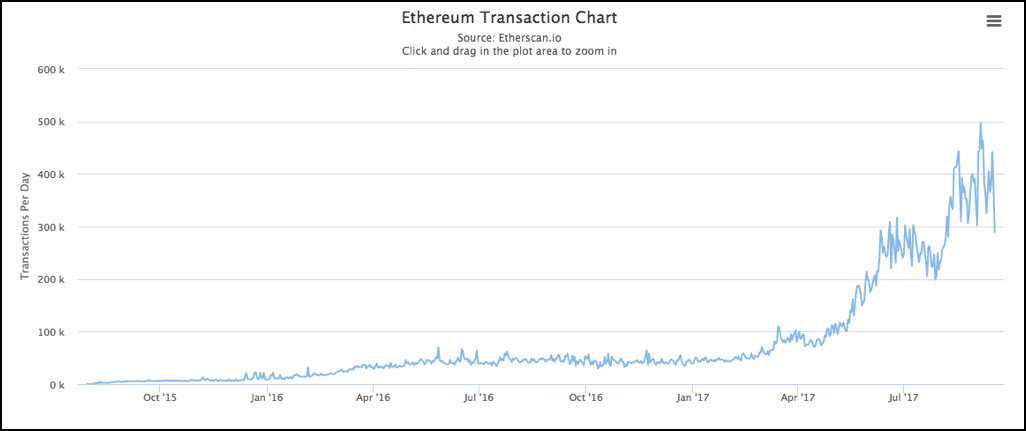
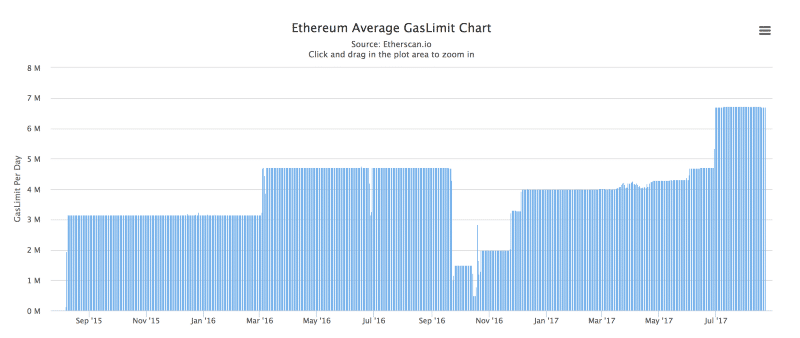
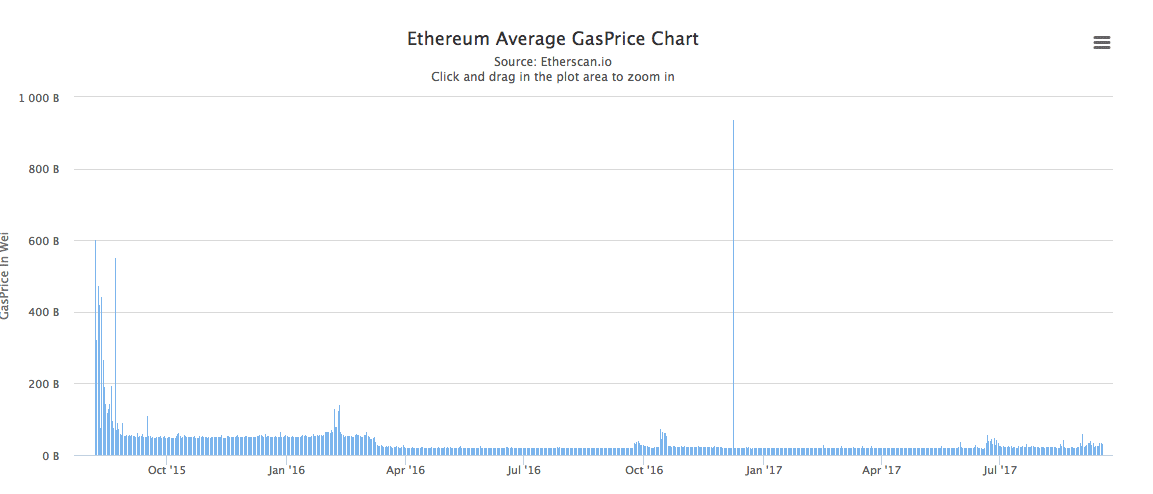
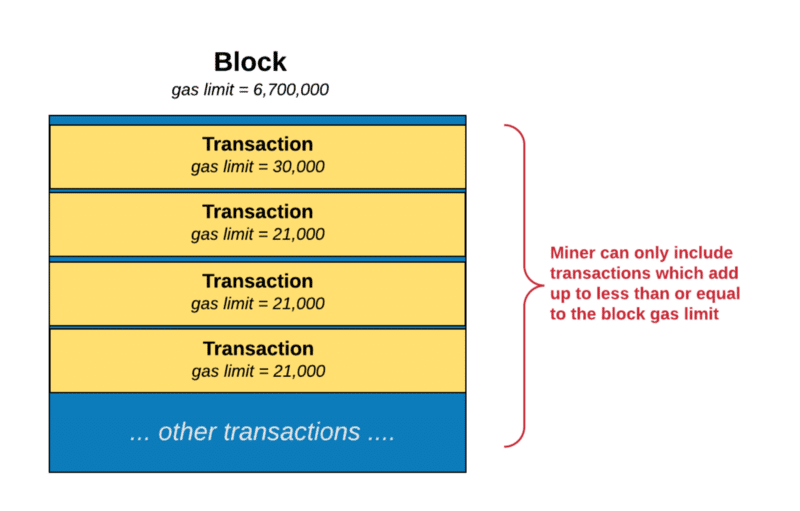


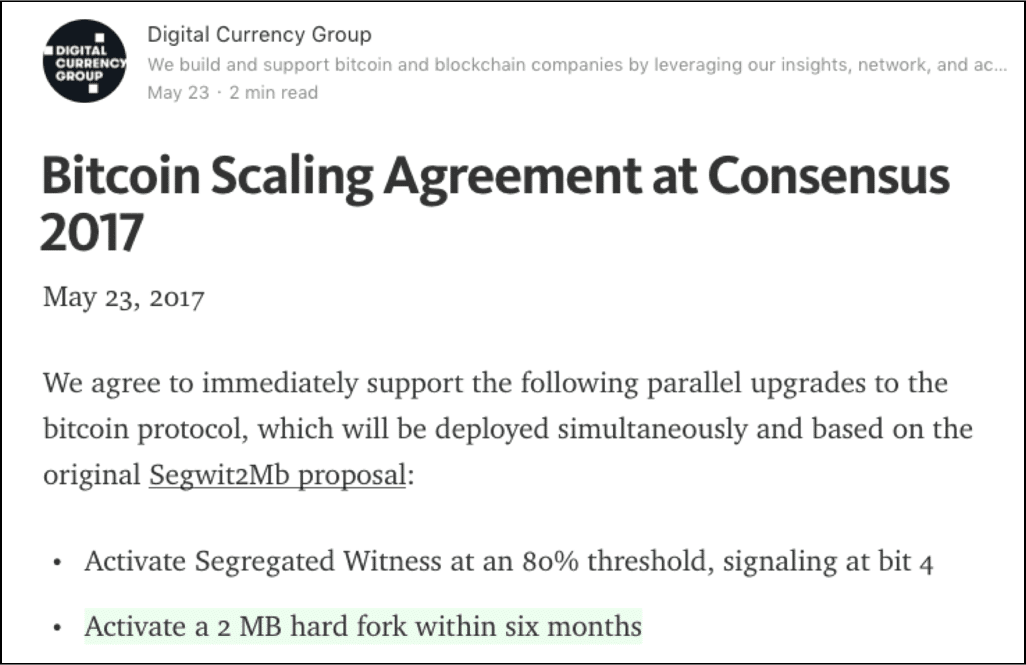
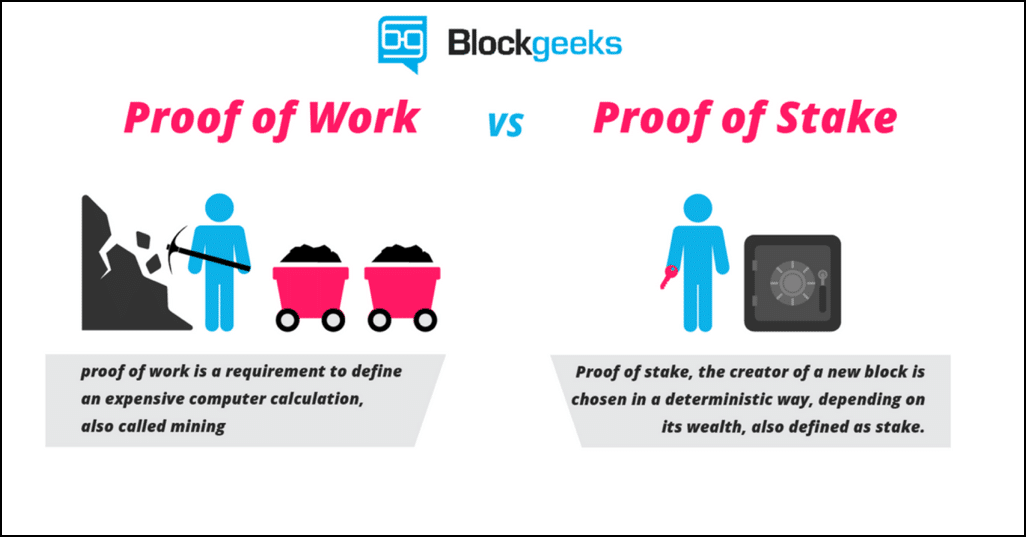
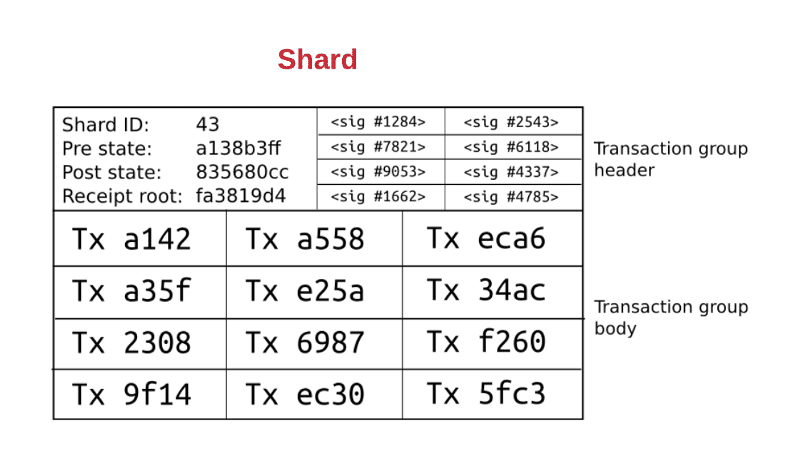
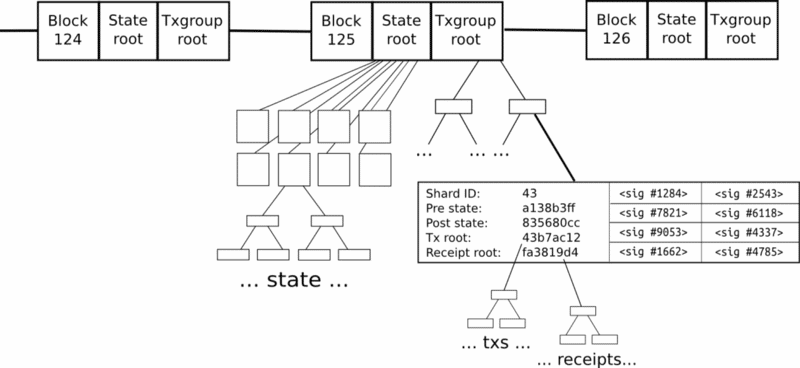
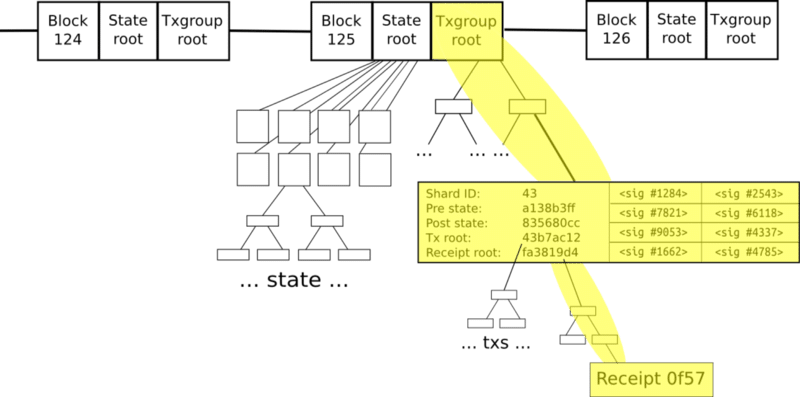
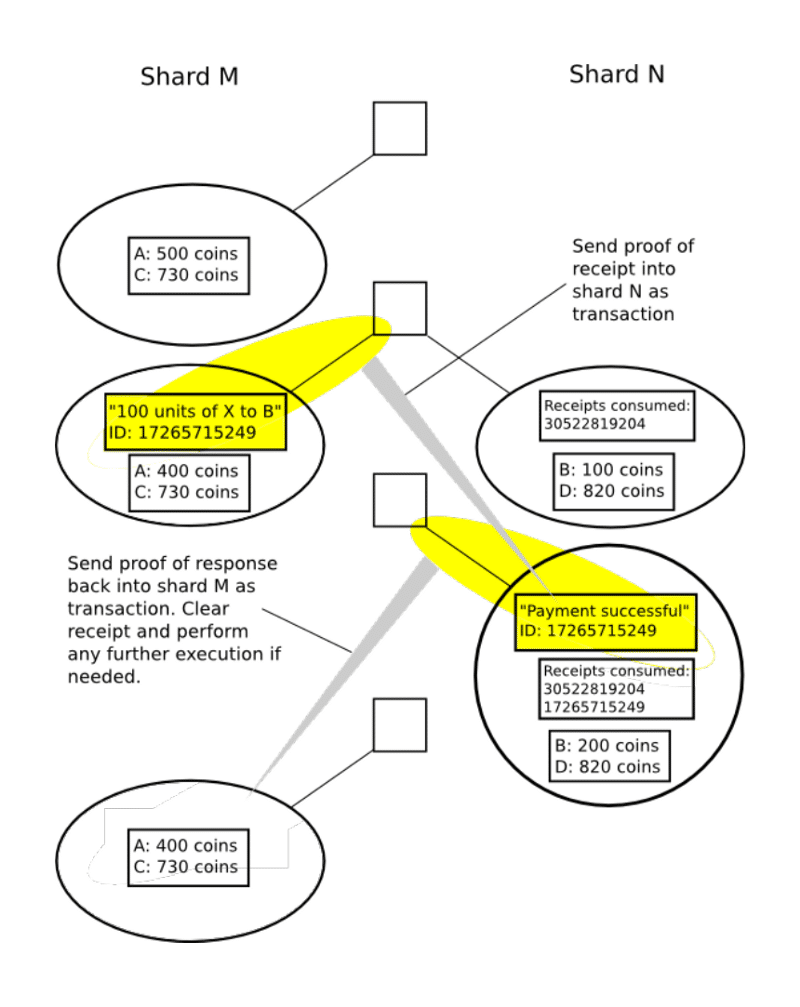
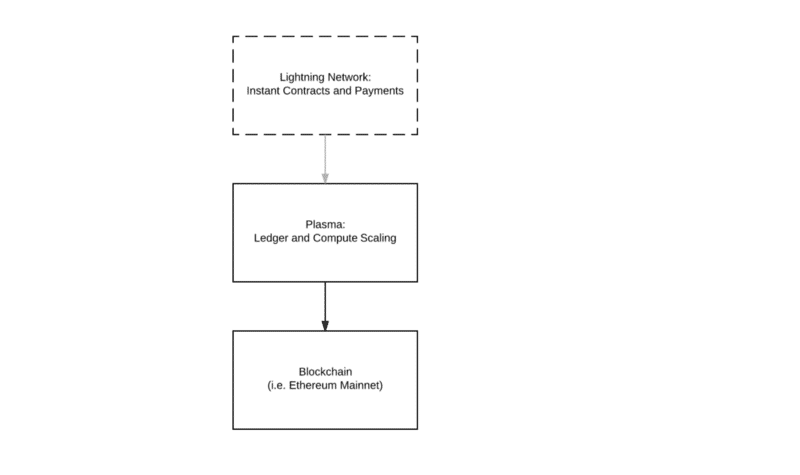
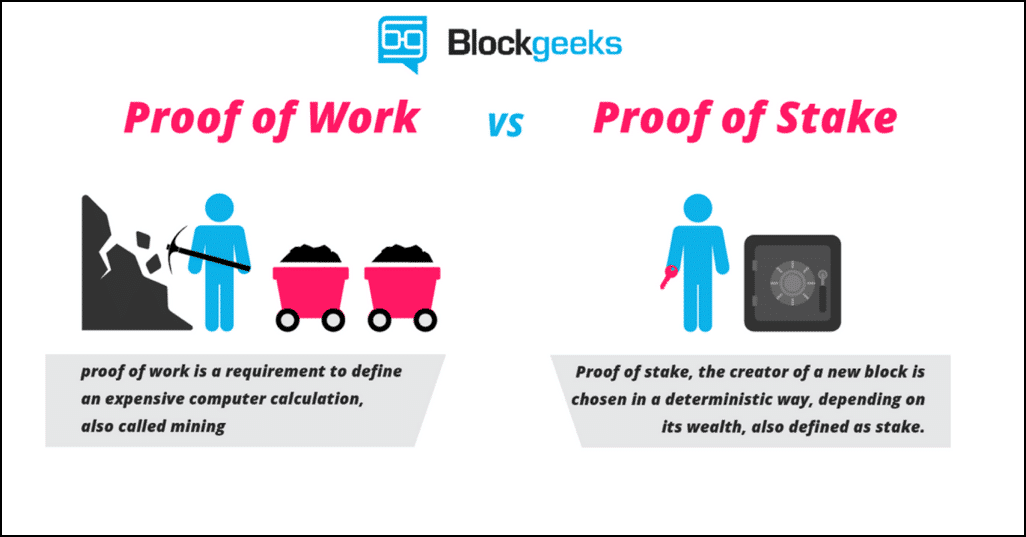
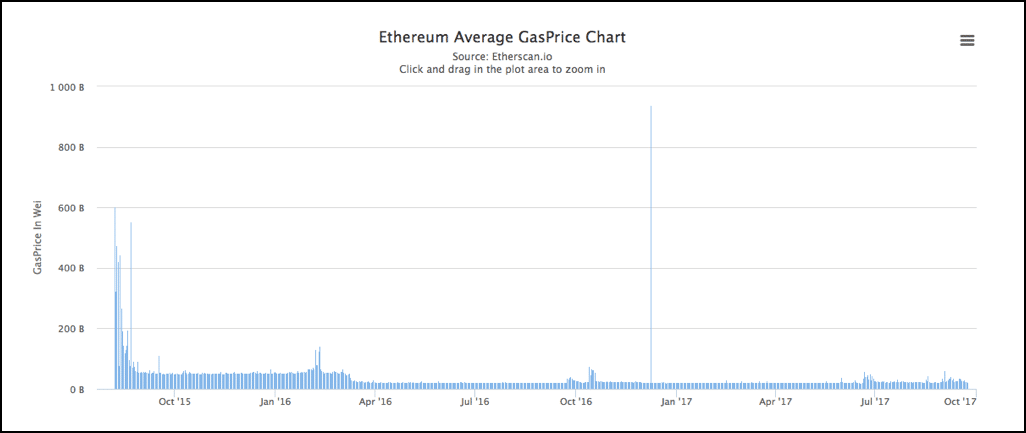
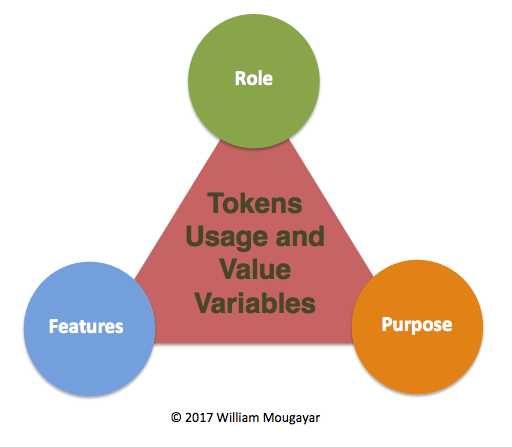
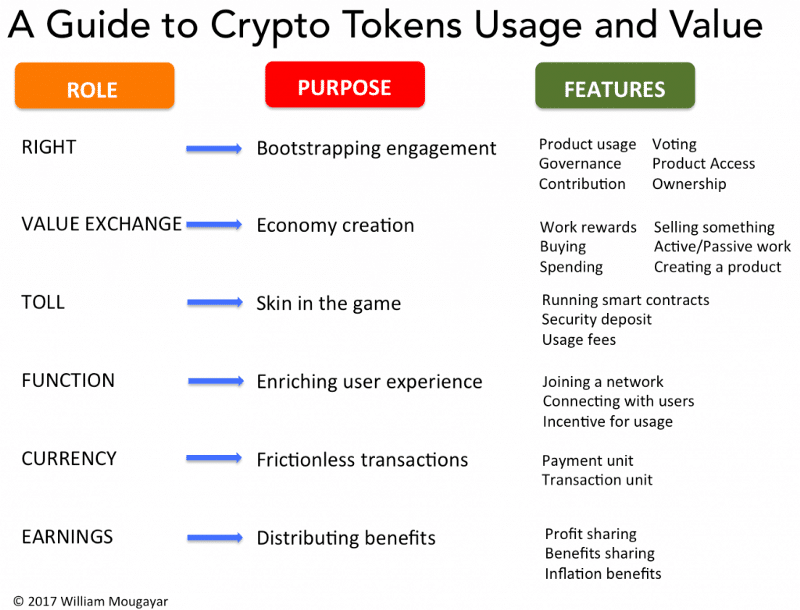
No comments:
Post a Comment
Note: Only a member of this blog may post a comment.